
Бесплатный фрагмент - The fourth industrial revolution glossarium: over 1500 of the hottest terms you will use to create the future
Textbook
FROM AUTHOR-CREATOR
Alexander Chesalov
Doctor of Engineering Sciences,
Corresponding member of the Russian Academy of Natural Sciences.
Specialist in the field of information technology and artificial intelligence since 1991.
Good afternoon, dear friends and colleagues!
Let me introduce you to my new book, «The Fourth Industrial Revolution Glossarium: over 1500 of the hottest terms you will use to create the future».
This is my new book, which combines the experience of the last five years in compiling concise dictionaries on the topics of the information technology, the artificial intelligence, the digital economy, the digital health, the Internet of things and, of course, my favorite topic — the fourth industrial revolution.
This story began in 2019, when I spoke at the world famous international conference TEDx with the report «The Fourth Industrial Revolution: through hardships to the stars».

Today, we are increasingly encountering such terms as: «fourth industrial revolution», «information society», «knowledge society», «digitalization» and «digital economy», «Internet of things» and «industrial Internet of things», «Internet of Value», «digital ecosystem», «robotics» and «artificial intelligence», and many others. And very often we do not understand what it is and cannot, for various reasons, understand the essence of modern «digital» processes that are happening to us and in the world around us.
I will give a simple example.
In this book, the «global information society» or «digital society of the future» is defined as a new global knowledge society that exists and interacts, and is also closely integrated into a fundamentally and qualitatively new «digital» social, economic and cultural ecosystem in which a free exchange of information and knowledge between people, using artificial intelligence, augmented and virtual reality, which are auxiliary interfaces for the interaction of people and machines, computers, robots, wearable and mobile devices, etc.

The global information society is a society of the future also because its development is based on intellect, information and knowledge, which are a catalyst for the emergence and development of new social, economic and including information technologies, which in turn transform both the information society itself, and the reality around us on the principle of a feedback system.
One example of the globalization of the information society and its gradual transformation is the widespread use in all areas of activity around the world of the technologies of the fourth industrial revolution. Robotics and artificial intelligence, new computing technologies and big data, digital platforms and ecosystems, new nano- and biotechnologies, and so on, they all unite all people around the world and are a catalyst for the «digital transformation» of modern society.
It is important to note that in the coming decades, the technologies of the fourth industrial revolution will radically change the way we perceive the world around us. They will change approaches to the processing and analysis of information, change the way people interact, change the processes of production of products and services, and, ultimately, form our new value systems. Humanity will have an understanding not only that information and big data are a value, but there will also be an understanding that they will largely determine the development of modern society. It can be said that right now the so-called «critical mass» of knowledge and technologies is being formed, which will «blow up» the world of technology and science, and change our daily life.
For many years I have been interested in robotics and artificial intelligence. Also, I was very interested in the direction of work — consumer robotics, or in simple terms, I was interested in the direction of creating humanoid robots that could help people, including those with disabilities, in their daily lives.

In 2007, robots were imperfect. Software for artificial intelligence systems based on machine learning was in its infancy. The intelligent assistants that we now often encounter when interacting with our smartphones have not yet been. And there is no need to talk about humanoid robots.
With the advent of the new millennium, the fourth industrial revolution changed the usual order of things.
Most of the modern terms of the fourth industrial revolution appeared in the period of the second and third industrial revolutions. I talk about this in detail in my book «Digital Transformation».
In an effort to use everything new, you and I must give ourselves an account of the fact that systems created on the basis of new technologies must first of all serve the interests of humanity, must give people more opportunities, more prospects, freedom and control over their own lives. And this is very important, because a person, sooner or later, will entrust the responsibility of managing and providing for his life to the «product» of his creativity, namely robots and artificial intelligence. And if you even look more broadly, at a number of robotic and automated systems controlled and serviced by hundreds of artificial intelligences, and not by humans.
The fourth industrial revolution is capable of generating any form of social, economic and cultural systems. And I would not like to share the opinion of Elon Musk that: «Artificial Intelligence will sooner or later kill all of us» or the opinion of the British physicist Stephen Hawking about the superiority of artificial intelligence over humanity. I share the view of our future offered by Klaus Martin Schwab in his books.

I would like to believe that you and I will be able to create such systems that will make our society more «humane», prosperous and allow us to increase the duration of our lives, open new opportunities for useful and interesting activities in a stable and harmoniously developing environment.
It is important to understand that the formation of the model of our future with you and the vital activity systems of our society, based on the use of technologies of the fourth industrial revolution, have not yet been implemented by anyone.
We are at the very beginning of the journey.

And, therefore, the question is how will our life with you change at the moment when the technologies of the fourth industrial revolution work in full force, what place will we occupy in this world, and most importantly — what role will be assigned to high technologies and results based on these technologies, depends exclusively on you and me!
What kind of book is this?
This is, first of all, an information guide that will help you or any other person, or a specialist from any industry, quickly enough to orientate yourself in the whole variety of new terms and definitions of the fourth industrial revolution.
The book is aimed not only at specialists working in the field of information technologies. The book is written for everyone who is interested in our future with you in the period of digital transformations of the fourth industrial revolution.
Why is the book called a «glossary»?
«Glossarium» in Latin means a dictionary of highly specialized terms.
My first experience in this area was in the compilation of a glossary on artificial intelligence and information technologies, which I published in December 2021. It originally contained only 400 terms. Then, already in 2022, I significantly expanded it to more than 1,000 relevant terms and definitions.
In 2022, in a team with two co-authors (with whom in 2021 I worked on the development of the Program of the Artificial Intelligence Center of the Bauman Moscow State Technical University), the “Glossary of artificial intelligence: 2,500 terms” was prepared and published. As it becomes clear from the title of the book, it already contains more than 2,500 terms and is defined in the direction of “artificial intelligence” in Russian and English. The first edition of this book was presented to a wide range of readers at the 35th Moscow International Book Fair in 2022.
In 2022, I completed another work and published the book “Glossary of digital economy: 1500 terms and definitions”, which helped me a lot in my daily work with the analysis of a huge amount of different information, when writing and implementing various IT projects.
In 2023, the book “Glossary on digital healthcare: 2000 terms and definitions” was published in the third year.
This book, as I said, combines experience from 2019 and was prepared by me for publication from 2021 to 2023. It contains terms and definitions that are widely used around the world. The book combines not only the best of the above books, but also includes terms and definitions from the topic of the Internet of Things and the fourth industrial revolution in general.
I, as the author-creator, do not claim authorship and uniqueness of the prepared text. The main goal of my work is to give you new and relevant information on the fourth industrial revolution, as well as a «tool» that will help you in your daily work.
The book is a personal project of the author and a completely free document for distribution. You are free to use this book however you like, but a link to the text in this book is required.
The book is published in electronic form, and I continue to work on improving and filling this book with new terms and definitions. I would be grateful for any feedback, suggestions and clarifications. Please send them to aleksander.chesalov@yandex.ru.
You can get to know me and my projects in the digital economy, artificial intelligence and IT systems in detail on my personal website chesalov.com.
This book is my gift to you.
Happy reading and productive work!
Yours, Alexander Chesalov.
03/15/2023. First edition. 1659 terms.
The Fourth Industrial Revolution Glossarium: over 1500 of the hotest terms you will use to create future
«A»
A/B testing — involves the testing of two variants in order to determine which one is better. For example, A/B testing can be used to find out which of two webpage options yields a better conversion rate. If it’s assumed that version A has a better conversion rate, it’s used as the basis for a new, slightly different version and then tested again to discover the better performing version.
Access Control — prevention of unauthorized use of a resource, including the prevention of use of a resource in an unauthorized manner.
Access history is a record of all activity related to an individual’s My Health Record. Every time My Health Record is accessed, changed or a user removes information from the record, an automatic audit trail is created and can be viewed.
Access in the context of security, is the privilege or assigned permission to use computer data or resources in some manner. For instance, a user may be allowed read access to a file, but will not be allowed to edit or delete it. Access is also the amount of admittance allowed to any given entity; or, it can simply mean the permission for admittance.
Access list is a list associated with an individual’s My Health Record that specifies the registered healthcare provider organizations permitted to, or blocked from, accessing an individual’s My Health Record. The access list will show the healthcare provider organizations who have previously accessed the record.
Access to information — the ability to obtain information and use it.
Access to information constituting a commercial secret — familiarization of certain persons with information constituting a commercial secret, with the consent of its owner or on other legal grounds, provided that this information is kept confidential.
Accessing organization — the healthcare organization that accesses the My Health Record system.
Accountable care organization (ACO) is an association of hospitals, healthcare providers and insurers in which all parties voluntarily assume financial and medical responsibility for medicare patients.
Achievement diary — developmental milestones throughout childhood, such as first words spoken or the first day of primary school, can be recorded in the achievement diary by an individual or their authorized representatives, such as a parent. Healthcare provider organizations cannot view these.
Active and Healthy Ageing is the process of optimizing opportunities related to health, participation and safety in order to improve quality of life.
Active assisted living (AAL) is concepts, products, services, and systems combining technologies and social environment with the aim of improving the quality of people’s lives.
Active Learning/Active Learning Strategy — a special case of Semi-Supervised Machine Learning in which a learning agent is able to interactively query an oracle (usually, a human annotator) to obtain labels at new data points. A training approach in which the algorithm chooses some of the data it learns from. Active learning is particularly valuable when labeled examples are scarce or expensive to obtain. Instead of blindly seeking a diverse range of labeled examples, an active learning algorithm selectively seeks the particular range of examples it needs for learning.
Adaptive Design is an alternative to responsive design and relies on creating a separate program design (mobile vs. desktop) for each view. Adaptive design is often referred to as dynamic serving. Responsive Design refers to the planning of an adaptive online service, in which the appearance of the service is designed to be responsive. A responsive online service uses one code from one web address to cater for the various devices a user has (desktop, tablet, smart phone, regular cell phone), but displays the content differently depending on the screen size,.
Adaptive system is a system that automatically changes the data of its functioning algorithm and (sometimes) its structure in order to maintain or achieve an optimal state when external conditions change.
Additive manufacturing (AM) or additive layer manufacturing (ALM) is the industrial production name for 3D printing, a computer-controlled process that creates three dimensional objects by depositing materials, usually in layers.
Additive technologies are technologies for the layer-by-layer creation of three-dimensional objects based on their digital models («twins»), which make it possible to manufacture products of complex geometric shapes and profiles.
Administration portal — an online tool used by the System Operator for administrative actions on individual My Health Records, for example when assisting an individual with an enquiry.
Advance care document custodian is someone who holds a copy of an individual’s advance care planning document. An individual can add their advance care document custodian’s name and contact details in their My Health Record so that doctors will be able to contact the custodian should the need arise.
Advance care planning documents is a document that is a type of written statement regarding a person’s wishes for their future medical or healthcare treatment and may formally appoint a substitute decision-maker. Advance care planning documents detail your future medical care preferences. It provides guidance to your family, close friends and medical professionals if you are unable to communicate due to illness or injury. Advance care planning documents (and goals of care documents) can be uploaded to and stored on your My Health Record by a healthcare provider with your consent. Also refer to Goals of Care document.
Advanced access controls — the access controls that enable a registered individual to set controls on the registered healthcare provider organizations and nominated representatives who may access the individual’s My Health Record or documents within it.
Agency for healthcare research and quality (AHRQ) is a U.S. government agency that functions as a part of the department of health & human services (HHS) to support research to help improve the quality of health care.
Aggregate — a total created from smaller units. For instance, the population of a county is an aggregate of the populations of the cities, rural areas, etc., that comprise the county. To total data from smaller units into a large unit.
Aggregate Data is data that have been aggregated. Contrast with microdata. Also, Aggregated Data — data of several individuals that have been combined to show general trends or values,.
Aggregator is a type of software that brings together various types of Web content and provides it in an easily accessible list. Feed aggregators collect things like online articles from newspapers or digital publications, blog postings, videos, podcasts, etc. A feed aggregator is also known as a news aggregator, feed reader, content aggregator or an RSS reader.
Agile Development is a group of methodologies used in software projects aimed at producing fit-for-purpose software faster and more reactively. Agile development can be understood as the opposite of traditional waterfall software development.
Agricultural Financial Platform is a center of excellence in agricultural finance in the form of a financing system for agricultural micro-enterprises, which includes practical tools for farmers, agricultural experts, financial practitioners, and knowledge and best practices for policy makers.
AI acceleration is acceleration of calculations encountered with AI, specialized AI hardware accelerators are allocated for this purpose (see also artificial intelligence accelerator, hardware acceleration). Also, AI acceleration is the acceleration of AI-related computations, for this purpose specialized AI hardware accelerators are used.
AI accelerator is a class of microprocessor or computer system designed as hardware acceleration for artificial intelligence applications, especially artificial neural networks, machine vision, and machine learning. Also, AI accelerator is a specialized chip that improves the speed and efficiency of training and testing neural networks. However, for semiconductor chips, including most AI accelerators, there is a theoretical minimum power consumption limit. Reducing consumption is possible only with the transition to optical neural networks and optical accelerators for them.
AI and machine learning imbues programs and machines with human-like decision-making capabilities. These capabilities become more advanced with machine learning algorithms and refined over time with exposure to larger data sets.
AI benchmark is an AI benchmark for evaluating the capabilities, efficiency, performance and for comparing ANNs, machine learning (ML) models, architectures and algorithms when solving various AI problems, special benchmarks are created and standardized, initial marks. For example, Benchmarking Graph Neural Networks — benchmarking (benchmarking) of graph neural networks (GNS, GNN) — usually includes installing a specific benchmark, loading initial datasets, testing ANNs, adding a new dataset and repeating iterations.
AI Building and Training Kits is applications and software development kits (SDKs) that abstract platforms, frameworks, analytics libraries, and data analysis appliances, allowing software developers to incorporate AI into new or existing applications.
AI camera — a camera with artificial intelligence, digital cameras of a new generation — allow you to analyze images by recognizing faces, their expression, object contours, textures, gradients, lighting patterns, which is taken into account when processing images; some AI cameras are capable of taking pictures on their own, without human intervention, at moments that the camera finds most interesting, etc.
AI chipset is a chipset for systems with AI, for example, AI chipset industry is an industry of chipsets for systems with AI, AI chipset market is a market for chipsets for systems with AI.
AI chipset market — chipset market for systems with artificial intelligence (AI), see also AI chipset.
AI cloud services are AI model building tools, APIs, and associated middleware that enable you to build/train, deploy, and consume machine learning models that run on a prebuilt infrastructure as cloud services. These services include automated machine learning, machine vision services, and language analysis services.
AI CPU is a central processing unit for AI tasks, synonymous with AI processor.
AI engineer is an AI systems engineer.
AI engineering — transfer of AI technologies from the level of R&D, experiments and prototypes to the engineering and technical level, with the expanded implementation of AI methods and tools in IT systems to solve real production problems of a company, organization. One of the strategic technological trends (trends) that can radically affect the state of the economy, production, finance, the state of the environment and, in general, the quality of life of a person and humanity.
AI hardware (also AI-enabled hardware) is infrastructure hardware or artificial intelligence system, AI infrastructure.
AI industry — for example, commercial AI industry — commercial AI industry, commercial sector of the AI industry.
AI industry trends are promising directions for the development of the AI industry.
AI infrastructure (also AI-defined infrastructure, AI-enabled Infrastructure) is the infrastructure of an artificial intelligence system, AI infrastructure, AI infrastructure, for example, AI infrastructure research — research in the field of AI infrastructures (see also AI, AI hardware).
AI server is a server with (based on) AI; a server that provides solving AI problems.
AI shopper is a non-human economic entity that receives goods or services in exchange for payment. Examples include virtual personal assistants, smart appliances, connected cars, and IoT-enabled factory equipment. These AIs act on behalf of a human or organization client.
AI supercomputer — a supercomputer for artificial intelligence tasks, a supercomputer for AI, characterized by a focus on working with large amounts of data (see also artificial intelligence, supercomputer).
AI term — a term from the field of AI (from terminology, AI vocabulary), for example, in AI terms — in terms of AI (in AI language) (see also AI terminology).
AI terminology is the terminology of artificial intelligence, a set of technical terms related to the field of AI.
AI TRiSM is the management of an AI model to ensure trust, fairness, efficiency, security, and data protection.
AI vendor is a supplier of AI tools (systems, solutions).
AI winter (Winter of artificial intelligence) is a period of reduced interest in the subject area, reduced research funding. The term was coined by analogy with the idea of nuclear winter. The field of artificial intelligence has gone through several cycles of hype, followed by disappointment and criticism, followed by a strong cooling off of interest, and then followed by renewed interest years or decades later.
AI workstation is a workstation (PC) with (based on) AI; AI RS, a specialized computer for solving technical or scientific problems, AI tasks; usually connected to a LAN with multi-user operating systems, intended primarily for the individual work of one specialist.
AI-based management system is the process of creating policies, allocating decision-making rights and ensuring organizational responsibility for risk and investment decisions for an application, as well as using artificial intelligence methods.
AI-based systems are information processing technologies that include models and algorithms that provide the ability to learn and perform cognitive tasks, with results in the form of predictive assessment and decision making in a material and virtual environment. AI systems are designed to work with some degree of autonomy through modeling and representation of knowledge, as well as the use of data and the calculation of correlations. AI-based systems can use various methodologies, in particular: machine learning, including deep learning and reinforcement learning; automated reasoning, including planning, dispatching, knowledge representation and reasoning, search and optimization. AI-based systems can be used in cyber-physical systems, including equipment control systems via the Internet, robotic equipment, social robotics and human-machine interface systems that combine the functions of control, recognition, processing of data collected by sensors, as well as the operation of actuators in the environment of functioning of AI systems.
AI-complete — in the field of artificial intelligence, the most difficult problems are informally known as AI-complete or AI-hard, implying that the difficulty of these computational problems is equivalent to that of solving the central artificial intelligence problem — making computers as intelligent as people, or strong AI. To call a problem AI-complete reflects an attitude that it would not be solved by a simple specific algorithm.
AI-enabled are tools with AI, using AI and equipped with AI (see also AI-enabled device). AI-enabled is AI-enabled hardware or software that uses AI-enabled AI, such as AI-enabled tools.
AI-enabled device is a device supported by an artificial intelligence (AI) system, such as an intelligent robot.
AI-enabled healthcare device is an AI-enabled healthcare device.
AIOps (Artificial Intelligence for IT Operations) is the use of machine learning and other AI technologies to automate many processes that are currently done manually in an organization. AIOps is similar to MLOps in that it uses machine learning and other AI technologies to automate IT processes. It is different from MLOps in that the process automation occurs within an organization’s IT operations department instead of an organization’s machine learning and AI team. AIOps is also different from MLOps because it uses AI to automate many processes, not just one or two tasks like MLOps does.
AI-optimized is one that is optimized for AI tasks or optimized using AI tools, for example, an AI-optimized chip is a chip that is optimized for AI tasks (see also artificial intelligence).
AlexNet is the name of a neural network that won the ImageNet Large Scale Visual Recognition Challenge in 2012. It is named after Alex Krizhevsky, then a computer science PhD student at Stanford University. See ImageNet.
Algorithm — an exact prescription for the execution in a certain order of a system of operations for solving any problem from some given class (set) of problems. The term «algorithm» comes from the name of the Uzbek mathematician Musa Al-Khorezmi, who in the 9th century proposed the simplest arithmetic algorithms. In mathematics and cybernetics, a class of problems of a certain type is considered solved when an algorithm is established to solve it. Finding algorithms is a natural human goal in solving various classes of problems. Algorithm is a set of instructions for solving a problem or accomplishing a task. One common example of an algorithm is a recipe, which consists of specific instructions for preparing a dish or meal. Every computerized device uses algorithms to perform its functions in the form of hardware- or software-based routines. In finance, algorithms have become important in developing automated and high-frequency trading (HFT) systems, as well as in the pricing of sophisticated financial instruments like derivatives.
Algorithm Economy is a term for the evolution of microservices and the functionality of algorithms to drive sophisticated application designs. The term is based on the utility of the algorithm in machine learning, artificial intelligence and other processes where software evolves beyond the limits of its original programming through the use of smart algorithm design. In the algorithm economy, companies can buy, sell or trade individual algorithms or pieces of an application. This decentralization of services is a more precise market than the market for full applications — for instance, applications that can share functional algorithms lead to more versatility for developers and more competition in markets.
Algorithmic Assessment is a technical evaluation that helps identify and address potential risks and unintended consequences of AI systems across your business, to engender trust and build supportive systems around AI decision making.
All.Can — initiative to identify ways to optimize the efficiency of cancer care by focusing on improving outcomes for patients and identifying inefficient practices, using technology to demonstrate how efficient care happens.
Allscripts is a vendor of electronic health record systems for physician practices, hospitals and healthcare systems.
AlphaGo (Программа AlphaGo) is the first computer program that defeated a professional player on the board game Go in October 2015. Later in October 2017, AlphaGo’s team released its new version named AlphaGo Zero which is stronger than any previous human-champion defeating versions. Go is played on 19 by 19 board which allows for 10171 possible layouts (chess 1050 configurations). It is estimated that there are 1080 atoms in the universe.
Ambient Computing is the evolution and combination of gesture and voice interfaces, speech recognition, cloud computing, wearable computing, IoT, augmented reality, AI and machine learning, and the quantified self.
Ambient intelligence (AmI) represents the future vision of intelligent computing where explicit input and output devices will not be required; instead, sensors and processors will be embedded into everyday devices and the environment will adapt to the user’s needs and desires seamlessly. AmI systems, will use the contextual information gathered through these embedded sensors and apply Artificial Intelligence (AI) techniques to interpret and anticipate the users’ needs. The technology will be designed to be human centric and easy to use.
Ambulatory medical record (AMR) is an electronically stored file of a patient’s outpatient medical records, which includes all surgeries and care that do not involve being admitted to a hospital.
American health information management association (AHIMA) is a professional organization that promotes the business and clinical uses of electronic and paper-based medical information.
American medical association (AMA) is a physician group that works for healthcare reform and publishes a collection of medical journals.
An initial coin offering (ICO) is the cryptocurrency industry’s equivalent of an initial public offering (IPO). A company seeking to raise money to create a new coin, app, or service can launch an ICO as a way to raise funds.
Analytics is a systematic analysis of information (data) or statistics for the discovery, communication, and interpretation of meaningful data patterns for better decision-making.
Anokhin’s theory of functional systems is a functional system consists of a certain number of nodal mechanisms, each of which takes its place and has a certain specific purpose. The first of these is afferent synthesis, in which four obligatory components are distinguished: dominant motivation, situational and triggering afferentation, and memory. The interaction of these components leads to the decision-making process.
Anonymization — process of removing all elements allowing the identification of an individual person (i.e., of rendering data anonymous). ISO/TS 25237:2008: process that removes the association between the identifying data set and the data subject. UK Information Commissioner’s Office: process of rendering data into a form which does not identify individuals and where identification is not likely to take place.
Anonymized Data — data which was identifiable when collected but which are not identifiable anymore (have been rendered anonymous). Anonymous data are no longer personal data. UK Information Commissioners Office: data in a form that does not identify individuals and where identification through its combination with other data is not likely to take place.
Antivirus software is a program or set of programs that are designed to prevent, search for, detect, and remove software viruses, and other malicious software like worms, trojans, adware, and more.
Anytime algorithm — an algorithm that can return a valid solution to a problem even if it is interrupted before it ends.
API economy is a business model where the use of application programming interfaces, or APIs, takes center stage. By using APIs, a company can, for instance, make their business processes or data available to others.
API-AS-a-service (AaaS) is an approach that combines API economy and software rental and provides application programming interfaces as a service.
App Economy refers to the range of economic activity surrounding mobile applications. Mobile apps created new fortunes for entrepreneurs and changed the way business is done. The app economy encompasses the sale of apps, ad revenue or public relations generated by free apps, and the hardware devices on which apps are designed to run. Apps have helped shape the leaders in mobile technology. Apple Inc., which was first out of the gate with the promotion of its App Store in 2008, gained a large chunk of market share with its iPhone. Apps were part of the iPhone’s initial draw. Android has since gained ground with its Android Market, which peddles apps for Android-based phones. Apps are also affecting a shift for online businesses, which are often accessed through an app on a mobile device, rather than over the Web. As a result, websites that get most of their revenue through online ads have had to consider what apps mean to their business model.
Application (application program) is a software program that runs on your computer such as Web browsers, e-mail programs, word processors, games, and utilities. The word «application» is used because each program has a specific application for the user.
Application Domain is a functional domain for application logic implementation.
Application Programming Interface (API) is a way for computers to talk to hardware or software platforms in a less complicated way. Also, Application programming interface or API is a communication channel through which two pieces of software (e.g. two digital platforms) can exchange information in a technical manner. APIs are central to the API economy and the platform economy, for instance,.
Application security is the process of making apps more secure by finding, fixing, and enhancing the security of apps. Much of this happens during the development phase, but it includes tools and methods to protect apps once they are deployed. This is becoming more important as hackers increasingly target applications with their attacks.
Apprenticeships — the learning model of «master and apprentice» is centuries old. Today, it is an increasingly common skills development policy employed by governments around the world. Apprenticeships involve a mixture of paid employment alongside job-specific training. Historically, apprenticeships have been concentrated in blue collar jobs, such as manufacturing. However, there are growing opportunities in professional services — such as banking, accounting, and consulting.
Architectural description group (Architectural view) is a representation of the system as a whole in terms of a related set of interests.
Architectural frameworks are high-level descriptions of an organization as a system; they capture the structure of its main components at varied levels, the interrelationships among these components, and the principles that guide their evolution.
Architecture of a computer is a conceptual structure of a computer that determines the processing of information and includes methods for converting information into data and the principles of interaction between hardware and software.
Architecture of a computing system is the configuration, composition and principles of interaction (including data exchange) of the elements of a computing system.
Architecture of a system is the fundamental organization of a system, embodied in its elements, their relationships with each other and with the environment, as well as the principles that guide its design and evolution.
Archival Information Collection (AIC) is information, the content of which is an aggregation of other packages of archival information. The digital preservation function preserves the capability to regenerate the DIPs (Dissemination Information Packages) as needed over time.
Archival Storage is a source for data that is not needed for an organization’s everyday operations, but may have to be accessed occasionally. By utilizing an archival storage, organizations can leverage to secondary sources, while still maintaining the protection of the data. Utilizing archival storage sources reduces primary storage costs required and allows an organization to maintain data that may be required for regulatory or other requirements.
Archive is a site where machine-readable materials are stored, preserved, and possibly redistributed to individuals interested in using the materials. To place or store in an archive.
Artifact is one of many kinds of tangible by-products produced during the development of software. Some artifacts (e.g., use cases, class diagrams, and other Unified Modeling Language (UML) models, requirements and design documents) help describe the function, architecture, and design of software. Other artifacts are concerned with the process of development itself — such as project plans, business cases, and risk assessments.
Artificial intelligence (AI) is a computer program that is able to perform intelligent operations independently. Artificial intelligence is difficult to define, since giving an exhaustive definition of intelligence is already challenging. Artificial intelligence (AI) refers to the simulation of human intelligence in machines that are programmed to think like humans and mimic their actions. The term may also be applied to any machine that exhibits traits associated with a human mind such as learning and problem-solving,.
Artificial intelligence (Artificial intelligence, Machine intelligence, AI) is the ability of a machine to make decisions and perform tasks that mimic human intelligence and behavior. Artificial intelligence is also called a complex of technological solutions that allows simulating human cognitive functions (including self-learning and searching for solutions without a predetermined algorithm) and obtaining results when performing specific tasks that are at least comparable to the results of human intellectual activity. The complex of technological solutions includes information and communication infrastructure, software (including those that use machine learning methods), processes and services for data processing and finding solutions.” Artificial intelligence is also given the following definition: AI is a computer system based on a set of scientific and engineering knowledge, as well as technologies for creating intelligent machines, programs, services and applications (for example, machine learning and deep learning), imitating the thought processes of a person or living beings, capable of perceiving information with a certain degree of autonomy, learning and making decisions based on the analysis of large amounts of data, the purpose of which is to help people solve their daily routine tasks. The term AI was first coined by John McCarthy in 1956,.
Artificial Intelligence Automation Platforms is platforms that enable the automation and scaling of production-ready AI. Artificial Intelligence Platforms involves the use of machines to perform the tasks that are performed by human beings. The platforms simulate the cognitive function that human minds perform such as problem-solving, learning, reasoning, social intelligence as well as general intelligence. Top Artificial Intelligence Platforms: Google AI Platform, TensorFlow, Microsoft Azure, Rainbird, Infosys Nia, Wipro HOLMES, Dialogflow, Premonition, Ayasdi, MindMeld, Meya, KAI, Vital A.I, Wit, Receptiviti, Watson Studio, Lumiata, Infrrd.
Artificial intelligence engine (also AI engine, AIE) is an artificial intelligence engine, a hardware and software solution for increasing the speed and efficiency of artificial intelligence system tools.
Artificial Intelligence for IT Operations (AIOps) is an emerging IT practice that applies artificial intelligence to IT operations to help organizations intelligently manage infrastructure, networks, and applications for performance, resilience, capacity, uptime, and, in some cases, security. By shifting traditional, threshold-based alerts and manual processes to systems that take advantage of AI and machine learning, AIOps enables organizations to better monitor IT assets and anticipate negative incidents and impacts before they take hold. AIOps is a term coined by Gartner in 2016 as an industry category for machine learning analytics technology that enhances IT operations analytics covering operational tasks include automation, performance monitoring and event correlations, among others. Gartner define an AIOps Platform thus: “An AIOps platform combines big data and machine learning functionality to support all primary IT operations functions through the scalable ingestion and analysis of the ever-increasing volume, variety and velocity of data generated by IT. The platform enables the concurrent use of multiple data sources, data collection methods, and analytical and presentation technologies”,, .
Artificial Intelligence Markup Language (AIML) is an XML dialect for creating natural language software agents.
Artificial Intelligence Open Library is a set of algorithms designed to develop technological solutions based on artificial intelligence, described using programming languages and posted on the Internet.
Artificial intelligence system (AIS) is a programmed or digital mathematical model (implemented using computer computing systems) of human intellectual capabilities, the main purpose of which is to search, analyze and synthesize large amounts of data from the world around us in order to obtain new knowledge about it and solve them. basis of various vital tasks. The discipline «Artificial Intelligence Systems» includes consideration of the main issues of modern theory and practice of building intelligent systems.
Artificial intelligence technologies are technologies based on the use of artificial intelligence, including computer vision, natural language processing, speech recognition and synthesis, intelligent decision support and advanced methods of artificial intelligence.
Artificial life (Alife, A-Life) is a field of study wherein researchers examine systems related to natural life, its processes, and its evolution, through the use of simulations with computer models, robotics, and biochemistry. The discipline was named by Christopher Langton, an American theoretical biologist, in 1986. In 1987 Langton organized the first conference on the field, in Los Alamos, New Mexico. There are three main kinds of alife, named for their approaches: soft, from software; hard, from hardware; and wet, from biochemistry. Artificial life researchers study traditional biology by trying to recreate aspects of biological phenomena.
Artificial Narrow Intelligence (ANI) also known as weak or applied intelligence, represents most of the current artificial intelligent systems which usually focus on a specific task. Narrow AIs are mostly much better than humans at the task they were made for: for example, look at face recognition, chess computers, calculus, and translation. The definition of artificial narrow intelligence is in contrast to that of strong AI or artificial general intelligence, which aims at providing a system with consciousness or the ability to solve any problems. Virtual assistants and AlphaGo are examples of artificial narrow intelligence systems,.
Artificial Neural Network (ANN) is a computational model in machine learning, which is inspired by the biological structures and functions of the mammalian brain. Such a model consists of multiple units called artificial neurons which build connections between each other to pass information. The advantage of such a model is that it progressively «learns» the tasks from the given data without specific programing for a single task.
Artificial neural networks (ANNs) usually simply called neural networks (NNs) are computing systems inspired by the biological neural networks that constitute animal brains. An ANN is based on a collection of connected units or nodes called artificial neurons, which loosely model the neurons in a biological brain. Each connection, like the synapses in a biological brain, can transmit a signal to other neurons. An artificial neuron receives signals then processes them and can signal neurons connected to it. The «signal» at a connection is a real number, and the output of each neuron is computed by some non-linear function of the sum of its inputs. The connections are called edges. Neurons and edges typically have a weight that adjusts as learning proceeds. The weight increases or decreases the strength of the signal at a connection. Neurons may have a threshold such that a signal is sent only if the aggregate signal crosses that threshold. Typically, neurons are aggregated into layers. Different layers may perform different transformations on their inputs. Signals travel from the first layer (the input layer), to the last layer (the output layer), possibly after traversing the layers multiple times.
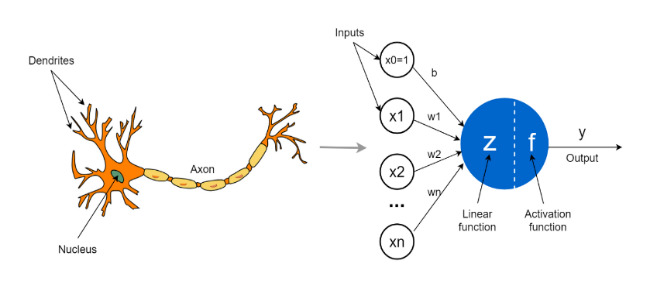
Artificial neuron is a mathematical function conceived as a model of biological neurons, a neural network. The difference between an artificial neuron and a biological neuron is shown in the figure.
Artificial neurons are the elementary units of an artificial neural network. An artificial neuron receives one or more inputs (representing excitatory postsynaptic potentials and inhibitory postsynaptic potentials on nerve dendrites) and sums them to produce an output signal (or activation, representing the action potential of the neuron that is transmitted down its axon). Typically, each input is weighted separately, and the sum is passed through a non-linear function known as an activation function or transfer function. Transfer functions are usually sigmoid, but they can also take the form of other non-linear functions, piecewise linear functions, or step functions. They are also often monotonically increasing, continuous, differentiable, and bounded,.
Artificial Superintelligence (ASI) is a term referring to the time when the capability of computers will surpass humans. «Artificial intelligence,» which has been much used since the 1970s, refers to the ability of computers to mimic human thought. Artificial superintelligence goes a step beyond and posits a world in which a computer’s cognitive ability is superior to a human.
ASCII is a character-encoding scheme used by many computers. The ASCII standard uses 7 of the 8 bits in a byte to define the codes for 128 characters. Example: In ASCII, the number «7» is treated as a character and is encoded as: 00010111. Because a byte can have a total of 256 possible values, there are an additional 128 possible characters that can be encoded into a byte, but there is no formal ASCII standard for those additional 128 characters. Most IBM-compatible personal computers do use an IBM «extended» character set that includes international characters, line and box drawing characters, Greek letters, and mathematical symbols. (ASCII stands for American Standard Code for Information Interchange).
Asset are mission-critical systems, physical hardware, applications, support systems, high-impact programs, personnel, equipment, locations, and more.
Asset framework is a hierarchy tree depicting the high level assets, sub assets, and individual sensors at the leaf level of the tree.
Assist — assessment and evaluation tools for e-service deployment in health, care and ageing — is an assessment and evaluation framework and tool built by Empirica for assessing the economic sustainability of telemedicine and telehealth services. Originally developed and successfully applied for business case development in telemedicine on behalf of the European Space Agency, the ASSIST tool exists also in adaptations for use in integrated eCare and eHealth services.
Assisted registration — the process that enables healthcare providers to assist their patients to register for a My Health Record.
Assisted Registration Tool (ART) — purpose-built software to enable an HPI-O to assert a patient’s identity and then submit their details to the My Health Record system for registration.
Assistive intelligence is AI-based systems that help make decisions or perform actions.
Assistive technology (AT) is any item, piece of equipment, software program, or product system that is used to increase, maintain, or improve the functional capabilities of persons with disabilities.
Association for the Advancement of Artificial Intelligence (AAAI) — an international, nonprofit, scientific society devoted to promote research in, and responsible use of, artificial intelligence. AAAI also aims to increase public understanding of artificial intelligence (AI), improve the teaching and training of AI practitioners, and provide guidance for research planners and funders concerning the importance and potential of current AI developments and future directions.
Assumed Consent — informational consent done in the absence of any formal recorded or verbal indication of agreement or any overt action (or inaction) on the part of the data subject.
Assurance — activities designed to reach a measure of confidence. Assurance is different from audit, which is more concerned with compliance to formal standards or requirements.
Asynchronous inter-chip protocols are protocols for data exchange in low-speed devices; instead of frames, individual characters are used to control the exchange of data.
Athenahealth Inc. is a developer of cloud-based practice management, point-of-care mobile applications and electronic health record (EHR) systems for small to medium-sized (SMB) physician practices and hospitals.
Attack Surface refers to the system elements and interactions that are vulnerable to cyberattacks.
Attack Vector is a pathway by which a cybercriminal can gain access to an entity.
Attention mechanism is one of the key innovations in the field of neural machine translation. Attention allowed neural machine translation models to outperform classical machine translation systems based on phrase translation. The main bottleneck in sequence-to-sequence learning is that the entire content of the original sequence needs to be compressed into a vector of a fixed size. The attention mechanism facilitates this task by allowing the decoder to look back at the hidden states of the original sequence, which are then provided as a weighted average as additional input to the decoder.
Attributes (XML) (Атрибуты (XML)) XML elements can have attributes that further describe them, such as the following: <Price currency=«Euro»> 25.43 </Price> In the example above, «currency» is an attribute of «Price», and the attribute’s value is «Euro».
Audit — an independent examination of an effort to determine its compliance with a set of requirements. An audit may be carried out by internal or external groups.
Audit Trail is a record that can be interpreted by auditors to establish that an activity has taken place. Often, a chronological record of system activities to enable the reconstruction and examination of the sequence of events and/or changes in an event. An audit trail of system resource usage may include user login, file access, and triggers that indicate whether any actual or attempted security violations occurred.
Auditability — property that ensures that any action of any security subject on any security object may be examined in order to establish the real operational responsibilities.
Augmented and virtual reality enable the creation of immersive and interactive experiences using digital simulations. In a post-pandemic world, where buying takes place at a distance, serving up products virtually has never been so crucial.
Augmented Intelligence is the intersection of machine learning and advanced applications, where clinical knowledge and medical data converge on a single platform. The potential benefits of Augmented Intelligence are realized when it is used in the context of workflows and systems that healthcare practitioners operate and interact with. Unlike Artificial Intelligence, which tries to replicate human intelligence, Augmented Intelligence works with and amplifies human intelligence.
Augmented Reality (AR) is an enhanced version of the real physical world that is achieved through the use of digital visual elements, sound, or other sensory stimuli delivered via technology. It is a growing trend among companies involved in mobile computing and business applications in particular. Also, Augmented Reality (AR) refers to an interactive experience that blends together the virtual world and the real world. For example, visuals of a product or component can be overlaid onto the real world via a mobile phone or tablet, enabling users to visualize a virtual object in a real-world space,.
Augmented reality technologies are visualization technologies based on adding information or visual effects to the physical world by overlaying graphic and/or sound content to improve user experience and interactive features.
Authentication — process of reliably identifying security subjects by securely associating an identifier and authenticator.
Authoring organisation — the healthcare provider organisation that created the content of a document.
Authorization — permission to perform certain operations or use certain methods or services.
Authorization link is a link that connects a healthcare provider to a healthcare provider organisation so the healthcare provider can access the My Health Record system via the National Provider Portal on behalf of their organisation.
Authorized employee — an employee of a registered healthcare provider organisation who has been authorized by the organisation to use the My Health Record system and access an individual’s My Health Record on behalf of the organisation.
Authorized representative — someone who can apply for and manage a My Health Record on behalf of another person. For the purposes of the My Health Record system someone can be an authorized representative if they: Have parental responsibility for a person under 14; or Have legal authority to act on behalf of a person who is at least 14 and who is not capable of making his or her own decisions. If there is no one with parental responsibility or legal authority, a person who is otherwise appropriate to act on behalf of the individual can be an authorized representative. An individual can have more than one authorized representative.
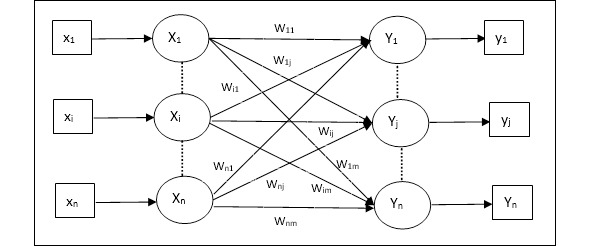
Auto Associative Memory is a single layer neural network in which the input training vector and the output target vectors are the same. The weights are determined so that the network stores a set of patterns. As shown in the following figure, the architecture of Auto Associative memory network has «n’ number of input training vectors and similar «n’ number of output target vectors.
Autoclave is a strong heated container used for chemical reactions and other processes using high pressures and temperatures, e.g., steam cleaning and sterilization.
Automata theory is the study of abstract machines and automata, as well as the computational problems that can be solved using them. It is a theory in theoretical computer science and discrete mathematics (a subject of study in both mathematics and computer science). Automata theory (part of the theory of computation) is a theoretical branch of Computer Science and Mathematics, which mainly deals with the logic of computation with respect to simple machines, referred to as automata,.
Automated control system is a set of software and hardware designed to control technological and (or) production equipment (executive devices) and the processes they produce, as well as to control such equipment and processes.
Automated is a machine that has been preprogrammed for a task, such as automated work order creation. While automated processes do not require outside control to complete the tasks for which they are programmed, automated processes do not have the ability to respond independently.
Automated processing of personal data — processing of personal data using computer technology.
Automated system is an organizational and technical system that guarantees the development of solutions based on the automation of information processes in various fields of activity.
Automation is a technology by which a process or procedure is performed with minimal human intervention.
Autonomic computing is the ability of a system to adaptively self-manage its own resources for high-level computing functions without user input.
Autonomous artificial intelligence is a biologically inspired system that tries to reproduce the structure of the brain, the principles of its operation with all the properties that follow from this.
Autonomous refers to a machine that 1) has the ability to self-govern or undertake actions without external control and 2) can respond independently to new information. One example is autonomous mobile robots (AMRs), which navigate without an operator, intelligently choosing the best path and avoiding obstacles.
Autonomous vehicle is a mode of transport based on an autonomous driving system. The control of an autonomous vehicle is fully automated and carried out without a driver using optical sensors, radar and computer algorithms.
Autonomy is an intelligent system’s ability to independently create and select different courses of action to achieve goals based on the system’s understanding and knowledge of the world and other factors.
Auxiliary intelligence — systems based on artificial intelligence that complement human decisions and are able to learn in the process of interacting with people and the environment.
Ayasdi is an enterprise scale machine intelligence platform that delivers the automation that is needed to gain competitive advantage from the company’s big and complex data. Ayasdi supports large numbers of business analysts, data scientists, end users, developers and operational systems across the organization, simultaneously creating, validating, using and deploying sophisticated analyses and mathematical models at scale.
«B»
B2B E-commerce refers to an online store for businesses. Normally, B2B (business-to-business) e-commerce is understood as an ordering system. The difference to a B2C online store targeting consumers is, for example, the requirement to identify the buyer through registering and the need to provide different billing options (such as invoicing).
B2C (business-to-consumer) E-commerce is a form of online commerce colloquially known as online shopping. B2C e-commerce refers to an online service that provides consumers with goods to purchase.
B2D (business-to-developer) marketing is an operational model that aims to engage software developers directly and by doing so affect customer acquisition. B2D marketing is a method of the platform economy which typically provides APIs in as developer-friendly form as possible to enable their proactive deployment.
B2D marketing is an operational model that aims to engage software developers directly and by doing so affect customer acquisition. B2D marketing is a method of the platform economy which typically provides APIs in as developer-friendly form as possible to enable their proactive deployment.
Backhaul refers to the process of reporting event information from tagged assets related to things like movement, temperature, distress and so forth.
Baldwin effect is the skills acquired by organisms during their life as a result of learning, after a certain number of generations, are recorded in the genome.
Bandwidth is the difference between the upper and lower frequencies in a continuous band of frequencies. It is typically measured in hertz, and depending on context, may specifically refer to passband bandwidth or baseband bandwidth. Passband bandwidth is the difference between the upper and lower cutoff frequencies of, for example, a band-pass filter, a communication channel, or a signal spectrum. Baseband bandwidth applies to a low-pass filter or baseband signal; the bandwidth is equal to its upper cutoff frequency. Bandwidth in hertz is a central concept in many fields, including electronics, information theory, digital communications, radio communications, signal processing, and spectroscopy and is one of the determinants of the capacity of a given communication channel. A key characteristic of bandwidth is that any band of a given width can carry the same amount of information, regardless of where that band is located in the frequency spectrum. Also, Bandwidth refers to the data throughput capacity of any communication channel. As bandwidth increases, more information per unit of time can pass through the channel,,.
Bar coded medication administration (BCMA) is a hospital inventory control system that uses barcodes in the distribution of prescription medications with the goal of ensuring the patient is receiving the correct medication.
Bayesian classifier in machine learning is a family of simple probabilistic classifiers based on the use of the Bayes theorem and the “naive” assumption of the independence of the features of the objects being classified.
Belief-desire-intention software model (BDI) is a software model developed for programming intelligent agents. Superficially characterized by the implementation of an agent’s beliefs, desires and intentions, it actually uses these concepts to solve a particular problem in agent programming. In essence, it provides a mechanism for separating the activity of selecting a plan (from a plan library or an external planner application) from the execution of currently active plans. Consequently, BDI agents are able to balance the time spent on deliberating about plans (choosing what to do) and executing those plans (doing it). A third activity, creating the plans in the first place (planning), is not within the scope of the model, and is left to the system designer and programmer.
Benchmarking is a set of techniques that allow you to study the experience of competitors and implement best practices in your company.
Beta release is a term that refers to a phase in online service development in which the service is coming together functionality-wise but genuine user experiences are required before the service can be finished in a user-centered way. In online service development, the aim of the beta phase is to recognize both programming issues and usability-enhancing procedures. The beta phase is particularly often used in connection with online services and it can be either freely available (open beta) or restricted to a specific target group (closed beta).
Bias is a systematic trend that causes differences between results and facts. Error exists in the numbers of the data analysis process, including the source of the data, the estimate chosen, and how the data is analyzed. Error can seriously affect the results, for example, when studying people’s shopping habits. If the sample size is not large enough, the results may not reflect the buying habits of all people. That is, there may be discrepancies between survey results and actual results.
Biased algorithm is systematic and repetitive errors in a computer system that lead to unfair results, such as one privilege persecuting groups of users over others. Also, sexist and racist algorithms.
Big Data analytics. As our world becomes digitized, vast quantities of data are generated and stored. This data holds hidden secrets that promise to revolutionize our understanding of the human condition. We need Big Data analytics to extract these insights.
Big Data is a term for sets of digital data whose large size, rate of increase or complexity requires significant computing power for processing and special software tools for analysis and presentation in the form of human-perceptible results. Also, Big Data refers to the collection, storage, sharing, searching, analyzing and presenting of enormous, unorganized and continuously growing masses of data with the help of statistics and information technology. As the Internet of Things and the Industrial Internet continue to spread, there is believed to be a growing demand for Big Data -related expertise. Big Data is a large amount of information about an organization (both structured and unstructured) that cannot be analyzed using traditional computing methods. Big Data in health refers to large routinely or automatically collected datasets which are electronically captured and stored. The data is reusable in the sense that it is multipurpose data. It involves the fusion and connection of existing databases for the purpose of improving health and health system performance. It does not refer to data collected for a specific study. Also, Big Data is data sets that are too large to be handled manually. Big Data must be analyzed by a computer, revealing patterns, associations between groups, or overall trends. Big Data also comes into systems in increasingly greater complexity, variety, volume, and velocity — and exponential increase over time,,,.
Binance Coin (BNB) is a utility cryptocurrency that operates as a payment method for the fees associated with trading on the Binance Exchange. It is the third-largest cryptocurrency by market capitalization.10 Those who use the token as a means of payment for the exchange can trade at a discount. Binance Coin’s blockchain is also the platform on which Binance’s decentralized exchange operates. The Binance Exchange was founded by Changpeng Zhao and is one of the most widely used exchanges in the world based on trading volumes.
Binance USD (BUSD) was created by the cryptocurrency exchange Binance as a stablecoin pegged to the U.S. dollar. The stablecoin was approved by the New York State Department of Financial Services; thus, it is also regulated.
Binary choice regression model is a regression model in which the dependent variable is dichotomous or binary. Dependent variable can take only two values and mean, for example, belonging to a particular group.
Binary format is any file format in which information is encoded in some format other than a standard character-encoding scheme. A file written in binary format contains information that is not displayable as characters. Software capable of understanding the particular binary format method of encoding information must be used to interpret the information in a binary-formatted file. Binary formats are often used to store more information in less space than possible in a character format file. They can also be searched and analyzed more quickly by appropriate software. A file written in binary format could store the number «7» as a binary number (instead of as a character) in as little as 3 bits (i.e., 111), but would more typically use 4 bits (i.e., 0111). Binary formats are not normally portable, however. Software program files are written in binary format. Examples of numeric data files distributed in binary format include the IBM-binary versions of the Center for Research in Security Prices files and the U.S. Department of Commerce’s National Trade Data Bank on CD-ROM. The International Monetary Fund distributes International Financial Statistics in a mixed-character format and binary (packed-decimal) format. SAS and SPSS store their system files in binary format.
Binary number is a number written using binary notation which only uses zeros and ones. Example: Decimal number 7 in binary notation is: 111.
Binary tree — a tree data structure in which each node has at most two children, which are referred to as the left child and the right child. A recursive definition using just set theory notions is that a (non-empty) binary tree is a tuple (L, S, R), where L and Rare binary trees or the empty set and S is a singleton set. Some authors allow the binary tree to be the empty set as well.
Bioconservatism (a portmanteau of biology and conservatism) is a stance of hesitancy and skepticism regarding radical technological advances, especially those that seek to modify or enhance the human condition. Bioconservatism is characterized by a belief that technological trends in today’s society risk compromising human dignity, and by opposition to movements and technologies including transhumanism, human genetic modification, «strong» artificial intelligence, and the technological singularity. Many bioconservatives also oppose the use of technologies such as life extension and preimplantation genetic screening,.
Biomedical informatics is the branch of health informatics that uses data to help clinicians, researchers and scientists improve human health and provide healthcare.
Biometrics is a system of recognizing people, by one or more physical or behavioral traits. In information technology, biometric data is used as a form of access ID management and access control.
Bio-Techno-System is a hybrid systems between biological systems and technical systems, by means of computer (science).
Bit is the smallest unit of information that a computer can work with. Each bit is either a «1» or a «0». Often computers work with groups of bits rather than one bit at a time; the smallest group of bits a computer usually works with is a byte, which is 8 bits.
Bitcoin is a cryptocurrency, a virtual currency designed to act as money and a form of payment outside the control of any one person, group, or entity, and thus removing the need for third-party involvement in financial transactions. It is rewarded to blockchain miners for the work done to verify transactions and can be purchased on several exchanges.
Bitcoin mining is the process of creating new bitcoin by solving puzzles. It consists of computing systems equipped with specialized chips competing to solve mathematical puzzles. The first bitcoin miner (as these systems are called) to solve the puzzle is rewarded with bitcoin. The mining process also confirms transactions on the cryptocurrency’s network and makes them trustworthy.
Blockchain is algorithms and protocols for decentralized storage and processing of transactions structured as a sequence of linked blocks without the possibility of their subsequent change. Also, Blockchain is used for cryptocurrency by using individual nodes that run a system for cryptocurrency exchanges. Exchanges of cryptocurrency are validated by miners. Miners validity is checked by other nodes for correctness. The use of blockchain technology reduces transaction times and fraud. Companies, such as Tesla, take cryptocurrency as a form of payment but do not accept all. In 2021, Tesla began accepting Bitcoin (BCH) then several months later stopped accepting due to environmental issues with mining of bitcoin. Tesla stopped accepting Bitcoin due to the environmental implications created by mining cryptocurrency. Cryptocurrency mining takes a substantial amount of electricity, generating a significant carbon footprint. Wit Bitcoin, there are several different types of crypto currencies including Ethereum (ETH), Litecoin (LTC), Cardano (ADA), Polkadot (DOT), Stellar (XLM), Dogecoin (DOGE), Biance Coin (BNB), Tether (USDT), Monero (XMR), with many more and a continuing amount of new currencies.
Blockchain Technology refers to the way in which operators that don’t know each other can produce and maintain decentralized databases. The technology allows for the members of the chain trust each other even though they don’t know one another. The best-known blockchain technology application is the virtual currency Bitcoin,.
Blocking of personal data — temporary cessation of processing of personal data (except for cases where processing is necessary to clarify personal data).
Blog (a truncation of «weblog») is a discussion or informational website published on the World Wide Web consisting of discrete, often informal diary-style text entries (posts). Posts are typically displayed in reverse chronological order, so that the most recent post appears first, at the top of the web page.
Blogger is someone who writes regularly for an online journal or website. A political blogger might provide weekly commentary on current events.
Blogosphere is the social universe created by online individuals using web log publishing platforms. Simply put, the blogosphere is a slang term for all the blogs on the internet. The blogosphere is often compared to grassroots journalism in that each member is able to post on any topic that catches their personal interest. The blogosphere is a powerful social network in that many popular bloggers have an audience measured in thousands and, in some cases, millions. However, the blogosphere is also very diverse, so the it does not represent a unified social unit — even though some of the social sub-groups within the blogosphere are. Post-based messaging services like Twitter are often considered part of the blogosphere despite the shorter length of the posts.
Bluetooth Low Energy (BLE) also known as Bluetooth 4.0, this is a wireless, personal-area network with short-range and low-power consumption that allows for objects to transmit data.
Boolean neural network is an artificial neural network approach which only consists of Boolean neurons (and, or, not). Such an approach reduces the use of memory space and computation time. It can be implemented to the programmable circuits such as FPGA (Field-Programmable Gate Array or Integrated circuit).
Born-digital is a descriptor for information that is created in digital form, as opposed to digitized from analog sources.
Brain Migration is a movement of highly-skilled professionals involved in intellectual or creative work as well as of potential specialists such as students and trainees going abroad for more than a year.
Brain technology (Also self-learning know-how system) is a technology that employs the latest findings in neuroscience. The term was first introduced by the Artificial Intelligence Laboratory in Zurich, Switzerland, in the context of the ROBOY project. Brain Technology can be employed in robots, know-how management systems and any other application with self-learning capabilities. In particular, Brain Technology applications allow the visualization of the underlying learning architecture often coined as «know-how maps».
Brain–computer interface (BCI), sometimes called a brain–machine interface (BMI), is a direct communication pathway between the brain’s electrical activity and an external device, most commonly a computer or robotic limb. Research on brain–computer interface began in the 1970s by Jacques Vidal at the University of California, Los Angeles (UCLA) under a grant from the National Science Foundation, followed by a contract from DARPA. The Vidal’s 1973 paper marks the first appearance of the expression brain–computer interface in scientific literature.
Brain-inspired computing is calculations on brain-like structures, brain-like calculations using the principles of the brain (see also neurocomputing, neuromorphic engineering).
Broadband refers to various high-capacity transmission technologies that transmit data, voice, and video across long distances and at high speeds. Common mediums of transmission include coaxial cables, fiber optic cables, and radio waves.
Brownfield refers to an existing industrial system targeted for new functionalities with zero operational disruptions.
Building Information Modelling (BIM) is a digital representation of physical and functional characteristics of places. A BIM is a shared knowledge resource for information about a place forming a reliable basis for decisions during its life-cycle; defined as existing from earliest conception to demolition.
Business administration (also known as business management) is the administration of a commercial enterprise. It includes all aspects of overseeing and supervising business operations. From the point of view of management and leadership, it also covers fields that include office building administration, accounting, finance, designing, development, quality assurance, data analysis, sales, project management, information-technology management, research and development, and marketing.
Business Blog (b-blog) is a blog of published, informal online articles that are either included in a company’s internal communications system (intranet) or posted on the Internet for the public to read. Business blogs use a more personal tone than corporate websites and are primarily used for public relations purposes. A business blog may also be referred to as a corporate blog or corporate Web log.
Business Continuity — «Describes the processes and procedures an organization puts in place to ensure that essential functions can continue during and after a disaster.» A note regarding preservation: Backups vs Preservation: Disaster recovery strategies and backup systems are not sufficient to ensure survival and access to authentic digital resources over time. A backup is a short-term data recovery solution following loss or corruption and is fundamentally different to an electronic preservation archive.
Business Design is a modern business model conceptualization. Business design is closely related to service design and shares some of its principles but applies them to the business concept of the entire company. The central idea of business design is to alter business activities in a customer-oriented manner in order to create strong customer loyalty.
Business Innovation is an organization’s process for introducing new ideas, workflows, methodologies, services or products. Like IT innovation, which calls for using technology in new ways to create a more efficient and agile organization, business innovation should enable the achievement of goals across the entire organization, with sights set on accomplishing core business aims and initiatives. Innovation often begins with idea generation, wherein ideas are narrowed down during brainstorming sessions, after which leaders consider the business viability, feasibility and desirability of each idea.
Business Intelligence refers to the applications, technologies, and practices for collecting, analyzing, and integrating business data to support improved business decision-making.
Business management tools are all the systems, applications, controls, calculating solutions, methodologies, etc. used by organizations to be able to cope with changing markets, ensure a competitive position in them and improve business performance.
Business mobility also known as enterprise mobility, is the growing trend of businesses to offer remote working options, allow the use of personal laptops and mobile devices for business purposes, and make use of cloud technology for data access. Business mobility recognizes a shift from the traditional central office business model.
Business model canvas is a representation of how an organisation makes (or intends to make) money. Based on an extensive literature research and real-world experience we define a business model as consisting of nine building blocks that constitute the business model canvas: 1. The value proposition of what is offered to the market; 2. The segment (s) of clients that are addressed by the value proposition; 3. The communication and distribution channels to reach clients and offer them the value? proposition; 4. The relationships established with clients; 5. The key resources needed to make the business model possible; 6. The key activities necessary to implement the business model; 7. The key partners and their motivations to participate in the business model; 8. The revenue streams generated by the business model (constituting the revenue model); 9. The cost structure resulting from the business model.
Business model describes the rationale of how an organization creates, delivers, and captures value, in economic, social, cultural or other contexts. The process of business model construction and modification is also called business model innovation and forms a part of business strategy. Also, Business model is a plan that identifies sources of revenue, the customer base, products, and details of financing. It simply tells how the business makes money,.
Business Payments Directory (BPD) is a system that enables online businesses to choose from a variety of trusted business payment vendors for whom they opt to contract out for managing their online sales payments and consumer purchases. Also known as an online payment’s directory.
Business to Business Gateway (B2B Gateway) is an access channel by which external systems, such as clinical information systems and registered repositories, interact with the My Health Record system.
Business Transaction in the context of electronic commerce, is any monetary transaction that is made between consumers or businesses via the Internet. Business transactions free up time when conducted online since each party does not need to be physically present in order to make the transaction.
Business use case is to describe, in technology free terminology, how a business process is used by people or systems external to the business to achieve their goals (composed from several definitions in the literature).
Business Viewpoint is an architecture viewpoint used to describe the purpose of establishing an IoT system by encompassing a business’s vision, mission, values, and objectives.
Byte is eight bits. A byte is simply a chunk of 8 ones and zeros. For example: 01000001 is a byte. A computer often works with groups of bits rather than individual bits and the smallest group of bits that a computer usually works with is a byte. A byte is equal to one column in a file written in character format.
«C»
C2C E-commerce refers to the selling of goods directly from one consumer to another online. Typically, an online service serves as a platform and enabler for this type of digital commerce.
Call center is a centralized department that handles inbound and outbound calls from current and potential customers. Call centers are located either within an organization or outsourced to another company that specializes in handling calls.
Call for Twinning Tenders is a DHE informational document on the purpose of twinning’s, twinning conditions, information on tendering and the evaluation and award criteria.
Call to Action (CTA) refers to a prompt that attracts the attention of a web page visitor and guides them to perform a desired action. A CTA is usually a link or an image which the visitor is supposed to click, or which requests the user’s email address or asks them to make a phone call. A CTA is one of the basic tools of conversion rate optimization.
Calm Technology is technology that does not affect life or the environment in which (or for which) it is produced.
Canonical Formats in information technology, canonicalization is the process of making something conform with some specification… and is in an approved format. Canonicalization may sometimes mean generating canonical data from noncanonical data. Canonical formats are widely supported and considered to be optimal for long-term preservation.
Capability — the organizational ability to intentionally and systematically use improvement approaches, methods and practices, to change processes and products/services to generate improved performance. The key word here is use. While capacity provides the potential for improvement, it is the active application and use of improvement approaches and practices that determine whether improved results will be realized.
Capacity (building) can be defined as the ability of individuals and organizations or organizational units to perform functions effectively, efficiently and sustainably. Capacity building is an evidence-driven process of strengthening the abilities of individuals, organizations, and systems to perform core functions sustainably, and to enable continuous improvement and development over time.
Capacity building framework. DHE WP3 developed a capacity building framework drawing on other existing frameworks which target all kinds of stakeholders who are interested in scaling-up person-centred digital solutions for integrated care. As part of this framework, 8 key components and 20 building blocks have been defined.
Capsule neural network (CapsNet) — a machine learning system that is a type of artificial neural network (ANN) that can be used to better model hierarchical relationships. The approach is an attempt to more closely mimic biological neural organization,.
Card image is eighty characters of data stored as a single physical record. A file storage format of 80 characters or bytes per record. The card-image format is a remnant of the time when data were literally input on punch cards that had physical limits of 80 characters per card. Usually a case or all the data for a single respondent is stored on several 80-character «cards.» Each «card» is numbered and stored in numerical sequence. Cards with the same sequence number (i.e., having a common format for the layout and contents of variables) are called a «deck»; thus, cards are often referred to in documentation by their «deck number». Example: «The variable for age is stored in Deck 01 in columns 10—11 and the variable for race is stored in Deck 02 in column 10».
Cardano (ADA) is a third-generation, decentralized proof-of-stake (PoS) blockchain platform designed to be a more efficient alternative to proof-of-work (PoW) networks. Scalability, interoperability, and sustainability on PoW networks like Ethereum are limited by the infrastructure burden of growing costs, energy use, and slow transaction times.
Care co-ordinator is an individual who is responsible for coordinating the care and support of a Care Recipient. It could be a role undertaken by a health care professional or the care recipient or family carer.
Care recipient is an individual who receives or seeks any care services or support considered to be integrated care, from another person or organisation. In certain circumstances, a care recipient may be the term used for a person receiving a new project-based service.
Case in survey research, an individual respondent.
Cashless Economy is a system where any type of money transactions is done through digital means like debit cards, electronic fund transfer, mobile payments, internet banking, mobile wallets.
Cashless society is one in which cash, in the form of physical banknotes and coins, is not accepted in any financial transaction. Instead, people and businesses transfer money to one another digitally — via credit or debit cards, electronic money transfers, cryptocurrency, or online and mobile payment services, such as PayPal and Apple Pay. Although no existing society is cashless, many economists believe that consumer preferences, competitive pressures on businesses, profit seeking by banks, and government policies designed to facilitate cashless transactions will soon lead to at least a few cashless societies.
Center for Technological Competence is an organization that owns the results, tools for conducting fundamental research and platform solutions available to market participants to create applied solutions (products) on their basis. The Technology Competence Center can be a separate organization or be part of an application technology holding company.
Centers for disease control and prevention (CDC) — promoting a healthy general public and sharing data about chronic diseases are main goals of the centers for disease control and prevention (CDC).
Centers for medicare & medicaid services (CMS) is the wing of the U.S. department of health and human services that runs healthcare reimbursement and health it programs.
Central processing unit (CPU) also called a central processor, main processor or just processor, is the electronic circuitry that executes instructions comprising a computer program. The CPU performs basic arithmetic, logic, controlling, and input/output (I/O) operations specified by the instructions in the program. This contrasts with external components such as main memory and I/O circuitry, and specialized processors such as graphics processing units (GPUs). Also, Central Processing Unit (CPU) is a von Neumann cyclic processor designed to execute complex computer programs.
Centralized control is a process in which control signals are generated in a single control center and transmitted from it to numerous control objects.
Cerner corp. is a public company in North Kansas City, mo., that provides various health information technologies, ranging from medical devices to electronic health records (EHR) to hardware.
Change Control is a formal process used to ensure that a process, product, service, or technology component is modified only in accordance with agreed-upon rules. Many organizations have formal Change Control Boards that review and approve proposed modifications to technology infrastructures, systems, and applications. Data Governance programs often strive to extend the scope of change control to include additions, modifications, or deletions to data models and values for reference/master data.
Change healthcare is a healthcare technology provider of revenue cycle management, payment management and health information exchange (HIE) solutions.
Channel is a means of entry into the My Health Record system to enable reading and updating My Health Records. For example, individuals can use the National Consumer Portal or providers may use the system via B2B.
Character format is any file format in which information is encoded as characters using only a standard character-encoding scheme. A file written in «character format» contains only those bytes that are prescribed in the encoding scheme as corresponding to the characters in the scheme (e.g., alphabetic and numeric characters, punctuation marks, and spaces).
Character-encoding scheme is a method of encoding characters including alphabetic characters (A-Z, uppercase and lowercase), numbers 0—9, punctuation and other marks (e.g., comma, period, space, &, *), and various «control characters» (e.g., tab, carriage return, linefeed) using binary numbers. For a computer to print a capital «A» or a number «7» on the computer screen, for instance, we must have a way of telling the computer that a particular group of bits represents an «A» or a «7». There are standards, commonly called «character sets,» that establish that a particular byte stands for an «A» and a different byte stands for a «7». The two most common standards for representing characters in bytes are ASCII and EBCDIC.
Chatbot is a software application designed to simulate human conversation with users via text or speech. Also referred to as virtual agents, interactive agents, digital assistants, or conversational AI, chatbots are often integrated into applications, websites, or messaging platforms to provide support to users without the use of live human agents. Chatbots originally started out by offering users simple menus of choices, and then evolved to react to particular keywords. “But humans are very inventive in their use of language,” says Forrester’s McKeon-White. Someone looking for a password reset might say they’ve forgotten their access code, or are having problems getting into their account. “There are a lot of different ways to say the same thing,” he says. This is where AI comes in. Natural language processing is a subset of machine learning that enables a system to understand the meaning of written or even spoken language, even where there is a lot of variation in the phrasing. To succeed, a chatbot that relies on AI or machine learning needs first to be trained using a data set. In general, the bigger the training data set, and the narrower the domain, the more accurate and helpful a chatbot will be.
Chief digital officer (CDO) is a leader who combines business acumen with digital expertise to help organizations drive digital transformation via an enterprise-wise digital vision and strategy.
Child development — the section of the My Health Record that contains information about childhood growth and development.
Chip is an electronic microcircuit of arbitrary complexity, made on a semiconductor substrate and placed in a non-separable case or without it, if included in the micro assembly.
CHRODIS Joint Action Recommendations and Criteria it constitutes a practical analytical framework that can be used by decision-makers, healthcare personnel, and patients to support the implementation of good practices, and to improve, monitor, and evaluate the quality of chronic disease prevention, health promotion and care.
Circular economy — an alternative to a traditional linear economy (make, use, dispose) in which we keep resources in use for as long as possible, extract the maximum value from them whilst in use, then recover and regenerate products and materials at the end of each service life.
Citizen agency is used meaning to inform, involve and enable citizens and communities to interact and influence authorities.
Civic and Community Engagement is an activity that includes activities such as volunteering, voting, and participating in activities that strengthen the community (City Library Council, 2017).
Classification are algorithms that allow machines to assign a category to a data point based on training data.
Cleaning is process to check data for adherence to standards, internal consistency, referential integrity, valid domain, and to replace/repair incorrect data with correct data. To «clean» a data file is to check for wild codes and inconsistent responses to verify that the file has the correct and expected number of records, cases, and cards or records per case; and to correct errors found.
Clinical decision support system (CDSS) is an application that analyzes data to help healthcare providers make decisions and improve patient care.
Clinical Document Architecture (CDA) is an HL7 standard intended to specify the encoding, structure and semantics of clinical documents for exchange.
Clinical documentation (healthcare) is the creation of a digital or analog record detailing a medical treatment, medical trial or clinical test.
Clinical informatics also known as health informatics, is the study of how technology and data analytics can be used to improve patient care plans.
Clinical information system (CIS) is a system that is used by a healthcare provider to manage patient and practice records. It may include a software component connected to the My Health Record system.
Clinical Patient Management System aims at supporting European Reference Networks in improving the diagnosis and treatment of rare or low prevalence complex diseases across national borders of Member States in Europe. The system enables healthcare professionals to upload patient cases and collaborate with other healthcare professionals to provide diagnosis, care and treatment.
Clinical synopsis is a short summary of a healthcare event (e.g. Reason for visit, diagnosis etc.) included in an event summary.
Clinical terminology guidelines — a set of terminological resources that can be implemented in software applications. They represent clinically relevant information in a semantically structured form of code that can be used by automated applications. These codes represent explicit formal definitions of meaning and are based on a consensus of actual use by clinicians.
Clinical Trial — any investigation in human subjects intended to discover or verify the effect of one or more investigational health interventions (e.g., drugs, diagnostics, devices, therapy protocols) that generate safety and efficacy data before making the health intervention available in health care.
Cloud Adoption refers to an organization’s move from its own servers and data centers to cloud-based solutions hosted by third parties. Cloud adoption is a strategic initiative for organizations, typically aimed at reducing costs, reducing risk and ensuring scalability. An organisation can move to the cloud, either in whole or in part, depending on its needs and its digital strategy.
Cloud Computing is a general term for anything that involves delivering hosted services over the internet. These services are divided into three main categories or types of cloud computing: infrastructure as a service (IaaS), platform as a service (PaaS) and software as a service (SaaS). Cloud Computing a model for enabling convenient, on-demand network access to a shared pool of configurable computing resources-for example networks, servers, storage, applications and services-that can be rapidly provisioned and released with minimal management effort or service provider interaction. Also, Cloud Computing is a term used to describe the delivery of computing services over the Internet,,.
Cloud deployment mode is the deployment of software on a cloud server outside an organization.
Cloud Infrastructure consists of hardware and software that enables cloud computing.
Cloud is software, services, or systems that are stored, managed, and accessed on demand via the Internet.
Cloud Service is a general term for a software service which is available over the Internet. Cloud service is a metaphor as it’s often depicted as a cloud in presentations. Previously, pieces of software were sold primarily as local software licenses, but it’s now common business practice to offer cloud services through software renting.
Cloud storage is computer data storage in which digital data is stored in servers generally located in multiple locations and owned and managed by a hosting company. These cloud storage providers are responsible for keeping the data available and accessible and the physical environment protected and running. People and organizations buy or lease storage capacity from the providers to store their data.
Cloud TPU is a specialized hardware accelerator designed to speed up machine learning workloads on Google Cloud Platform.
Cluster analysis is a type of unsupervised learning used for exploratory data analysis to find hidden patterns or groupings in the data; clusters are modeled with a similarity measure defined by metrics such as Euclidean or probability distance.
Cluster is a number of computers networked together in order to function as a single computing system.
Clustering is a task to organize data into groups based on certain properties. Clustering analysis is widely used in data mining for pattern recognition, image analysis, and computer graphics, among others.
CMIO (chief medical information officer) essentially serves as the bridge between medical and IT departments at a health care organization. This person may also be referred to as the director of medical informatics or health informatics.
Code in most numeric data files, answers to questions are recorded with numbers rather than text, and often even numeric answers are recorded with numbers other than the actual response. The numbers used in the data file are called «codes.» Thus, for instance, when a respondent identifies herself as a member of a particular religion, a code of «1» might be used for Catholic, a «2» for Jewish, etc. Likewise, a person’s age of 18 might be coded as a 2 indicating «18 or over.» The codes that are used and their correspondence to the actual responses are listed in a codebook. Code is a one-to-one mapping of a finite ordered set of symbols belonging to some finite alphabet.
Code of the digital transformation program event (carried out by a state body) — a unique character digital identifier of the program event, assigned in accordance with these Regulations to the program event and containing codified information about the main manager of the federal budget or the budgets of state non-budgetary funds — the state body implementing the program event, type of the program activity, its serial number, its version, as well as other characteristics necessary for the unambiguous identification of the program activity at all stages of its planning and implementation, including during the monitoring of the program implementation, carried out in accordance with the Regulation approved by Resolution No. 1646 «On measures to ensure the effectiveness of measures for the use of information and communication technologies in the activities of federal executive authorities and government agencies of state extrabudgetary jet funds.
Codebook generically, is any information on the structure, contents, and layout of a data file. Typically, a codebook includes: column locations and widths for each variable; definitions of different record types; response codes for each variable; codes used to indicate nonresponse and missing data; exact questions and skip patterns used in a survey; and other indications of the content of each variable. Many codebooks also include frequencies of response. Codebooks vary widely in quality and amount of information included.
Codec is the means by which sound and video files are compressed for storage and transmission purposes. There are various forms of compression: ’lossy’ and ’lossless’, but most codecs perform lossless compression because of the much larger data reduction ratios that occur [with lossy compression]. Most codecs are software, although in some areas codecs are hardware components of image and sound systems. Codecs are necessary for playback, since they uncompress [or decompress] the moving image and sound files and allow them to be rendered».
Cognitive architecture the Institute of Creative Technologies defines cognitive architecture as: «hypothesis about the fixed structures that provide a mind, whether in natural or artificial systems, and how they work together — in conjunction with knowledge and skills embodied within the architecture — to yield intelligent behavior in a diversity of complex environments».
Cognitive computing is used to refer to the systems that simulate the human brain to help with the decision- making. It uses self-learning algorithms that perform tasks such as natural language processing, image analysis, reasoning, and human–computer interaction. Examples of cognitive systems are IBM’s Watson and Google DeepMind.
Cognitive Maps are structured representations of decision depicted in graphical format (variations of cognitive maps are cause maps, influence diagrams, or belief nets). Basic cognitive maps include nodes connected by arcs, where the nodes represent constructs (or states) and the arcs represent relationships. Cognitive maps have been used to understand decision situations, to analyze complex cause-effect representations and to support communication.
Cognitive science are the interdisciplinary scientific study of the mind and its processes.
Collaboration platform — the concept behind the collaboration platforms is adopted from the 3C collaboration model developed by Borghoff and Schlichter that describes «Cooperation, Communication and Coordination as the main challenges for the members in a collaborative group» (Borghoff & Schlichter, 2000). Cooperation is the joint work production and completion of tasks, supported by tools such as joint document storage and repositories, wikis and notes keeping systems. Communication includes efficient exchange of information and negotiation of commitments via emails, instant messaging, discussion lists, and video- or phone conferences. Coordination enables people, activities and resources to be managed, leading to better communication and cooperation (e.g. staff and project management tools, scheduling tools, and the like). These tools will be adopted to ensure functional collaboration. The objectives of each collaboration platform are to identify relevant stakeholders and initiatives, engage with them to analyze key challenges and solutions related to each DTHC priority, elaborate common strategic agendas and commitments for action.
Collaborative robots are a type of machine that, unlike traditional ones, can work alongside humans without any safety risk. They perform numerous functions and are very adaptable, changing activity or working capacity according to the demand of the moment.
Column in a data file, a single vertical column, each being one byte in length. Fixed format data files are traditionally described as being arranged in lines and columns. In a fixed format file, column locations describe the locations of variables.
Column location — the precise location in a data file of a variable expressed in column numbers, beginning with the first column in a physical record as column number 1.
Commoditization is the process of transforming a product from an elite to a generally available (comparatively cheap commodity of mass consumption).
Common Services — the supporting services such as inter-process communication, name services, temporary storage allocation, exception handling, security, and directory services necessary to support.
Communication — enabling the digital transformation of health and care in the Digital Single Market; empowering citizens and building a healthier society.
Communication Platforms is digital media that are used as means of communication. In marketing, they provide information and awareness about a specific product or brand.
Competence an approach that for achievement of high results an employee must demonstrate labor behavior, which is possible if certain individually-psychological qualities or their complementary sets, which in this case is not crucial, because the assignment of an employee to the success or lack of success made only on demonstrated behavior. It is related to employment concept that says the professionalism on the sphere, in which the worker is competent. It is relative to the individual concept, which says about aspects of the behavior necessary for competent performance.
Competence is an approach that for achievement of high results an employee must demonstrate labor behavior, which is possible if certain individually-psychological qualities or their complementary sets, which in this case is not crucial, because the assignment of an employee to the success or lack of success made only on demonstrated behavior. It is related to employment concept that says the professionalism on the sphere, in which the worker is competent. It is relative to the individual concept, which says about aspects of the behavior necessary for competent performance.
Competitiveness of the state — the formation of obvious advantages in relation to other states in the scientific and technological field and, as a result, in the social, cultural, educational and economic fields.
Compiler is a program that translates text written in a programming language into a set of machine codes. AI framework compilers collect the computational data of the frameworks and try to optimize the code of each of them, regardless of the hardware of the accelerator. The compiler contains programs and blocks with which the framework performs several tasks. The computer memory resource allocator, for example, allocates power individually for each accelerator.
Compliance is a discipline, set of practices, and/or organizational group that deals with adhering to laws, regulations, standards, and contractual arrangements. Also, the adherence to requirements. Data Governance programs often support many types of compliance requirements: Regulatory compliance, contractual compliance, adherence to internal standards, policies, and architectures, and conformance to rules for data management, project management, and other disciplines.
Components of the information and telecommunications infrastructure — software and hardware complexes and tools shared by information systems that perform common technological functions and provide the basis for the operation of these information systems, including those that ensure their information and technological interaction.
Composable Business refers to the design, implementation and development of an enterprise’s digital infrastructure using business-level components (PCBs) that can be replaced according to market needs in a more flexible way than those based on a traditional monolithic architecture. The adoption of a composable business approach is usually aimed at gaining competitive advantage, resilience and adaptability.
Composable Commerce is an approach that selects the best software components and combines them into a customized application, offering functionality familiar from e-commerce. Composable commerce is therefore a set of e-commerce services built according to the principles of composable commerce.
Composite AI is the combined application of various AI techniques to improve learning efficiency, expand the level of knowledge representation and, ultimately, to more effectively solve a wider range of business problems.
Compression is a method of reducing the size of computer files. There are several compression programs available, such as gzip and WinZip.
Compression ratio or reduction ratio — the ratio that is used to discuss the quantity of original data versus the quantity of data after compression.
Computation is any type of arithmetic or non-arithmetic calculation that follows a well-defined model (e.g., an algorithm).
Computational creativity (Also artificial creativity, mechanical creativity, creative computing) is a multidisciplinary endeavor that includes the fields of artificial intelligence, cognitive psychology, philosophy, and the arts.
Computational cybernetics is the integration of cybernetics and computational intelligence techniques.
Computational efficiency of an agent or a trained model is the amount of computational resources required by an agent to solve a problem at the inference stage (data output from the model).
Computational efficiency of an intelligent system is the amount of computing resources required to train an intelligent system with a certain level of performance on a given volume of tasks.
Computational humor — a branch of computational linguistics and artificial intelligence which uses computers in humor research.
Computational intelligence (CI) — usually refers to the ability of a computer to learn a specific task from data or experimental observation.
Computational mathematics is the mathematical research in areas of science where computing plays an essential role.
Computational neuroscience (Also theoretical neuroscience or mathematical neuroscience) — a branch of neuroscience which employs mathematical models, theoretical analysis and abstractions of the brain to understand the principles that govern the development, structure, physiology, and cognitive abilities of the nervous system.
Compute modules — plug-in specialized computers designed to solve narrowly focused tasks, such as accelerating the work of artificial neural networks algorithms, computer vision, voice recognition, machine learning and other artificial intelligence methods, built on the basis of a neural processor — a specialized class of microprocessors and coprocessors (CPU, memory, data transfer).
Compute Units are blocks that act as a filter that transforms packets according to certain rules. The instruction set of the calculator can be limited, which guarantees a simple internal structure and a sufficiently high speed of operation.
Computer assisted coding system (CACS) is medical software that reviews healthcare forms, including electronic health records, and assigns appropriate medical codes to its findings.
Computer attack — a targeted impact of software and (or) software and hardware on critical information infrastructure objects, telecommunication networks used to organize the interaction of such objects, in order to disrupt and (or) stop their functioning and (or) create a threat to the security processed by such object’s information.
Computer engineering is technologies for digital modeling and design of objects and production processes throughout the life cycle.
Computer incident is a fact of violation and (or) cessation of the operation of a critical information infrastructure object, a telecommunication network used to organize the interaction of such objects, and (or) a violation of the security of information processed by such an object, including as a result of a computer attack.
Computer Network is a collection of interconnected endpoints in a many-to-many arrangement.
Computer programming is the process of performing a particular computation (or more generally, accomplishing a specific computing result), usually by designing and building an executable computer program. Programming involves tasks such as analysis, generating algorithms, profiling algorithms’ accuracy and resource consumption, and the implementation of algorithms (usually in a chosen programming language, commonly referred to as coding). The source code of a program is written in one or more languages that are intelligible to programmers, rather than machine code, which is directly executed by the central processing unit. The purpose of programming is to find a sequence of instructions that will automate the performance of a task (which can be as complex as an operating system) on a computer, often for solving a given problem. Proficient programming thus usually requires expertise in several different subjects, including knowledge of the application domain, specialized algorithms, and formal logic. Tasks accompanying and related to programming include testing, debugging, source code maintenance, implementation of build systems, and management of derived artifacts, such as the machine code of computer programs. These might be considered part of the programming process, but often the term software development is used for this larger process with the term programming, implementation, or coding reserved for the actual writing of code. Software engineering combines engineering techniques with software development practices.
Computer science is the theory, experimentation, and engineering that form the basis for the design and use of computers. She involves the study of algorithms that process, store, and communicate digital information. A computer scientist specializes in the theory of computation and the design of computational systems. Computer science is the study of computation, automation, and information. Computer science spans theoretical disciplines (such as algorithms, theory of computation, and information theory) to practical disciplines (including the design and implementation of hardware and software). Computer science is generally considered an area of academic research and distinct from computer programming.
Computer simulation is the process of mathematical modelling, performed on a computer, which is designed to predict the behavior of, or the outcome of, a real-world or physical system. The reliability of some mathematical models can be determined by comparing their results to the real-world outcomes they aim to predict. Computer simulations have become a useful tool for the mathematical modeling of many natural systems in physics (computational physics), astrophysics, climatology, chemistry, biology and manufacturing, as well as human systems in economics, psychology, social science, health care and engineering.
Computer vision (CV) is scientific discipline, field of technology and the direction of artificial intelligence (AI), which deals with computer processing, recognition, analysis and classification of dynamic images of reality. It is widely used in video surveillance systems, in robotics and in modern industry to improve product quality and production efficiency, comply with legal requirements, etc. In computer vision, the following areas are distinguished: face recognition (face recognition), image recognition (image recognition), augmented reality (augmented reality (AR) and optical character recognition (OCR). Synonyms — artificial vision, machine vision.
Computer vision processing (CVP) is the processing of images (signals) in a computer vision system, in computer vision systems — about algorithms (computer vision processing algorithms), processors (computer vision processing unit, CVPU), convolutional neural networks (convolutional neural network), which are used for image processing and implementation of visual functions in robotics, real-time systems, smart video surveillance systems, etc.
Computer-Assisted Telephone Interviewing (CATI) /Personal Interviewing (CAPI) is a method of coding information from telephone or personal interviews directly into a computer during the interview. CATI/CAPI software usually has built-in consistency checks, will not allow wild codes to be entered, and automatically prompts the interviewer for correct skip pattern questions.
Computerized Maintenance Management System (CMMS) Software is CMMS software, which can be either cloud-based or on-premise, is designed to enhance the efficiency and effectiveness of maintenance activities, such as planning, scheduling, and monitoring of work orders and maintenance needs. A CMMS can also serve as a centralized location for industrial data.
Computerized physician order entry (CPOE) also known as computerized provider order entry or computerized practitioner order entry, refers to the process of a medical professional entering and sending medication orders and treatment instructions electronically via a computer application instead of on paper charts.
Computing modules are plug-in specialized computers designed to solve narrowly focused tasks, such as accelerating the work of artificial neural networks algorithms, computer vision, voice recognition, machine learning and other artificial intelligence methods, built on the basis of a neural processor — a specialized class of microprocessors and coprocessors (processor, memory, data transfer).
Computing system — a software and hardware complex or several interconnected complexes that form a single infrastructure designed to solve problems and process data (including computing).
Computing units are blocks that work like a filter that transforms packets according to certain rules. The instruction set of the calculator can be limited, which guarantees a simple internal structure and a sufficiently high speed of operation.
Condition Monitoring (CM) — the process of monitoring various conditions associated with machine health, including vibration and temperature. Condition monitoring lets maintenance teams quickly identify when conditions exceed set thresholds for normal operation and resolve issues before failure occurs.
Confidentiality ensuring that information is accessible only to those authorized to have access.
Confidentiality of information is a mandatory requirement for a person who has access to certain information not to transfer such information to third parties without the consent of its owner.
Confirmation Bias is the tendency to search for, interpret, favor, and recall information in a way that confirms one’s own beliefs or hypotheses while giving disproportionately less attention to information that contradicts it.
Conformant digital certificate (for the My Health Record system) is an electronic credential used to secure access in the My Health Record system.
Connecting Europe Facility (CEF) is a key EU funding instrument to promote growth, jobs and competitiveness through targeted infrastructure investment at European level. It supports the development of high performing, sustainable and efficiently interconnected trans-European networks in the fields of transport, energy and digital services.
Connectivity Endpoint are interfaces that provide connectivity.
Connectivity is the ability of a device or system to connect to other systems, applications, or programs via the internet. Connectivity is the backbone of all IoT solutions.
Consent — any freely given specific and informed indication of his wishes by which the data subject signifies his agreement to personal data relating to him being processed.
Consistency check is a process of data cleaning that eliminates inappropriate responses to branched questions. For instance, one question might ask if the respondent attended church last week; a response of «no» should indicate that questions about church attendance should be coded as «inapplicable.» If those questions were coded any other way than «inapplicable,» this would be inconsistent with the skip patterns of the survey instrument.
Consolidated health informatics (CHI) initiative refers to a collaborative effort to create and adopt health informatics standards to be used by federal departments such as the department of health & human services and the department of veteran’s affairs.
Consortium is an association of research and production and marketing organizations headed by a leader organization created to achieve strategic goals and implement research and production projects and enter the markets. The consortium may include: higher education institutions, scientific organizations, developers of the component base and software, product manufacturers, constituent entities of the Russian Federation, development institutions and banks, consumers and other interested organizations.
Consumer artificial intelligence is specialized artificial intelligence programs embedded in consumer devices and processes.
Consumer Portal — the portal that is used by an individual who has set up access to their My Health Record online.
Consumer spending is the total money spent on final goods and services by individuals and households for personal use and enjoyment in an economy. Contemporary measures of consumer spending include all private purchases of durable goods, nondurable goods, and services. Consumer spending can be regarded as complementary to personal saving, investment spending, and production in an economy.
Consumer-shared documents — documents that have been authored by an individual, authorized representative or full access nominated representative. These documents, such as personal health summary, are available to provider organizations and other representatives.
Contact center is a central point from which organizations manage all customer interactions across various channels. Their primary purpose is to offer customers efficient and effective technical support, customer service and sales assistance.
Content industry is an umbrella term that encompasses companies owning and providing mass media and media metadata. This can include music and movies, text publications of any kind, ownership of standards, geographic data, and metadata about all and any of the above.
Context data includes manufacturing process information about quality, maintenance events, operational events, environmental conditions, and process performance. This information typically resides in external business applications.
Continuity of care document (CCD) is an electronic document exchange standard for sharing patient summary information.
Continuity of care record (CCR) is a standard for the creation of electronic summaries of patient health. Its aim is to improve the quality of health care and to reduce medical errors by making current information readily available to physicians.
Contracted service provider (CSP) officer — the officer who acts as the liaison between a registered contracted service provider and the System Operator. There must be at least one CSP officer and there can be up to three at one time.
Control Domain are functional domains for industrial control system implementations.
Control is a means of managing a risk or ensuring that an objective is achieved. Controls can be preventative, detective, or corrective and can be fully automated, procedural, or technology-assisted human-initiated activites. They can include actions, devices, procedures, techniques, or other measures.
Conversion means the completion of a measured action on a web page. A successful conversion can involve subscribing to a newsletter, filling out a contact form or buying a product from an online store. Conversion rate optimization is used to improve the conversion rate, given as a percentage.
Conversion Rate Optimization (CRO) refers to the editing of a web page with the aim of improving the conversion rate of the page. CRO is usually an inevitable form of business development for consumer online stores, since even the smallest enhancement in the conversion rate has a direct impact on sales.
Convolution is the process of filtering. A filter (or equivalently: a kernel or a template) is shifted over an input image. The pixels of the output image are the summed product of the values in the filter pixels and the corresponding values in the underlying image.
Convolutional neural network (CNN) is a type of neural network that identifies and interprets images.
Cookie is a file or segment of data that identifies a unique user over time and across interactions with a website, sent by the web server through a browser, stored on a user’s hard drive, and sent back to the server each time the browser requests a web page.
Corelet programming environment is a scalable environment that allows programmers to set the functional behavior of a neural network by adjusting its parameters and communication characteristics.
Correlation analysis is a statistical data processing method that measures the strength of the relationship between two or more variables. Thus, it determines whether there is a connection between the phenomena and how strong the connection between these phenomena is.
Correlation is a statistical relationship between two or more random variables.
Cost-benefit analysis is a way of assessing the impact of a program or a measure by weighing the advantages (benefits) against the disadvantages (costs).
Cost-effectiveness analysis — analysis that calculates and compares the costs and effects of two or more interventions, allowing to establish priorities among them.
Costs of Distance Education are the main cost variables such as technological infrastructure and educational processes that influence the achievement of the goals set by educational institutions providing distance education services.
Counterparty — a party to a civil law contract to which the owner of information constituting a trade secret has transferred this information.
Critical information infrastructure is objects of critical information infrastructure, as well as telecommunication networks used to organize the interaction of such objects.
Critical information infrastructure objects — information systems and information and telecommunication networks of state bodies, as well as information systems, information and telecommunication networks and automated process control systems operating in the defense industry, in the field of healthcare, transport, communications, in the credit and financial sector, energy, fuel, nuclear, rocket and space, mining, metallurgical and chemical industries.
Critical information infrastructure of the Russian Federation is a set of critical information infrastructure objects, as well as telecommunication networks used to organize the interaction of critical information infrastructure objects with each other.
Cross-border health care means health care provided or prescribed in a Member State other than the Member State of affiliation (i.e. Member State competent to give authorization to receive treatment outside the Member State of residence).
Cross-border information exchange means the process of sending and receiving information across legislative boundaries using interoperable systems in order to read and further process this information in a meaningful way.
Cross-border transfer of personal data — transfer of personal data to the territory of a foreign state to the authority of a foreign state, a foreign individual or a foreign legal entity.
Cross-Cutting Concern impacts an entire system and may also affect multiple architectural viewpoints.
Cross-Cutting Function is one that can be applied across multiple functional architectural domains to address cross-cutting concerns.
Cross-sectional study in survey research is a study in which data from particular subjects are obtained only once. Contrast with longitudinal studies, in which a panel of individuals is interviewed repeatedly over a period of time. Note that questions in a cross-sectional study can apply to previous time periods.
Crowdfunding is a way of raising money to finance projects and businesses. It enables fundraisers to collect money from a large number of people via online platforms.
Crowdsourcing is the practice of getting ideas or help on a project from a large number of people, usually through the Internet.
CRUD — Create, Read, Update, Delete. Used to describe access rights for data.
Cryogenic freezing (cryonics, human cryopreservation) is a technology of preserving in a state of deep cooling (using liquid nitrogen) the head or body of a person after his death with the intention to revive them in the future.
Cryptocurrency broadly defined, is virtual or digital money that takes the form of tokens or «coins.» Though some cryptocurrencies have ventured into the physical world with credit cards or other projects, the large majority remain entirely intangible.
Cryptocurrency exchange, or a digital currency exchange (DCE) is a business that allows customers to trade cryptocurrencies or digital currencies for other assets, such as conventional fiat money or other digital currencies. Exchanges may accept credit card payments, wire transfers or other forms of payment in exchange for digital currencies or cryptocurrencies. A cryptocurrency exchange can be a market maker that typically takes the bid–ask spreads as a transaction commission for is service or, as a matching platform, simply charges fees.
Cryptography — the mathematical science that deals with transforming data to render its meaning unintelligible (i.e., to hide its semantic content), prevent its undetected alteration, or prevent its unauthorized use. If the transformation is reversible, cryptography also deals with restoring encrypted data to intelligible form. Also, Cryptography exemplifies the means, principles, and mechanisms for data transformation to hide information to prevent its undetected modification or unauthorized use,.
Current procedural terminology (CPT) code are a uniform medical code set maintained and copyrighted by the American medical association and used to describe medical, surgical and diagnostic services.
Customer Data Integration is an approach to managing multiple records containing information about an organization’s customers. In this approach, instead of combining all information into a single repository, a combination of technologies, processes and services are used to align information in multiple repositories.
Customer Experience (CX) is the sum of encounters experienced by a customer in various digital and traditional media. In the digital era, the significance of ensuring a positive customer experience is highlighted since the buyer may come across an organization in various contexts. Encounters are provided by web pages, newspapers, radio, television and social media channels, among others. An organization should aim at providing a consistent customer experience through these encounters, to ensure the desired outcome (for example, a purchase or a recommendation).
Customer Journey Tracking (analysis of user behavior) — the term designates the data-based analysis of buying decision processes. If the customer buys online, it is possible to reconstruct the decision-making path of the client using special tracking tools. For example, when using the tool it is possible to find out how many advertising contacts were necessary to activate the purchase of a specific product.
Customer relationship management (CRM) is the combination of practices, strategies and technologies that companies use to manage and analyze customer interactions and data throughout the customer lifecycle. The goal is to improve customer service relationships and assist in customer retention and drive sales growth. CRM systems compile customer data across different channels, or points of contact, between the customer and the company, which could include the company’s website, telephone, live chat, direct mail, marketing materials and social networks. CRM systems can also give customer-facing staff members detailed information on customers’ personal information, purchase history, buying preferences and concerns.
Cyberattack is any offensive maneuver that targets computer information systems, computer networks, infrastructures, or personal computer devices. An attacker is a person or process that attempts to access data, functions, or other restricted areas of the system without authorization, potentially with malicious intent. Depending on the context, cyberattacks can be part of cyber warfare or cyberterrorism. A cyberattack can be employed by sovereign states, individuals, groups, society, or organizations, and it may originate from an anonymous source.
Cybercrime also called computer crime, the use of a computer as an instrument to further illegal ends, such as committing fraud, trafficking in child pornography and intellectual property, stealing identities, or violating privacy. Cybercrime, especially through the Internet, has grown in importance as the computer has become central to commerce, entertainment, and government.
Cyber-Physical Production Systems (CPPS) it is when physical and digital items are connected, monitored and managed with computer programming and algorithms.
Cyber-physical systems are intelligent networked systems with built-in sensors, processors and drives that are designed to interact with the physical environment and support the operation of computer information systems in real time; cloud computing is an information technology model for providing ubiquitous and convenient access using the information and telecommunications network «Internet» to a common set of configurable computing resources («cloud»), data storage devices, applications and services that can be promptly provided and relieved from the load with minimal operating costs or almost without the participation of the provider.
Cyber-resilience this is a «new» term, and only used in specific contexts of modern business challenges. Check it out the World Economic Forum definition: At its simplest, being cyber-resilient means taking measures to prevent and protect against the criminal or unauthorized use of electronic data. As digital transformation gathers pace, Cyber-resilience will move up the world’s agenda. The number of data breaches is increasing, as is the severity of the attacks. Based on the Gemalto Breach Level Index, the first half of 2018 saw 945 data breaches affecting 4.5 billion records, a 133% increase over the same period last year. More than 90% of events involved unencrypted data and 65% identity theft. A significant number of breaches involved government records. The Forum recently published the 2018 Global Risk report, showing the increasing risks to cybersecurity over the past decade. More pointedly a respondent pool of 12,500 companies covering the three largest regions of North America, Europe and EAPAC named digital Cyber-resilience as the biggest global risk. Business, government and citizens all stand to lose if we cannot create a safe digital environment to capture the potential gains from the Fourth Industrial Revolution.
Бесплатный фрагмент закончился.
Купите книгу, чтобы продолжить чтение.
