
Бесплатный фрагмент - Risks in E-Commerce
Introduction
In the modern world, it is difficult to imagine life without the possibility of online purchases, money transfers, electronic wallets and bank cards. The popularity of using cryptocurrencies is actively gaining momentum. The e-commerce market is now only at the beginning of its formation, but it is becoming sustainable, which has tightly occupied its niche. In the near and long term, the trend of increasing payments in the digital space is very clear. Banks, international payment systems, processing centers and payment aggregators traditionally play a key role in this market. You should also not forget about other participants: bank card holders, merchants, holders of electronic money and cryptocurrencies. All together, they are intertwined in a single payment process, in various combinations and schemes.
Of course, the interaction of various parties to the process always carries certain risks, as a rule, for everyone, just to a lesser or greater extent, not to mention a separate category of participants — scammers. Yes, they are also an integral part of any payment market and can act on behalf of any person, starting from the cardholder and ending with a bank or other financial institution.
In the first chapter, the reader can get acquainted with the general structure and types of risks. The following chapters will be devoted to the details and ways to minimize these risks, as well as methods of countering fraudulent actions.
Chapter 1.
The main risks,
their schematic representation
and description
In order to consider the main risks, it is necessary first to determine the understanding of what to put into the concept of «risk».
We will consider a certain event as a risk, which entails negative consequences expressed in one form or another. This concept has two characteristics: the probability of occurrence, or simply probability and consequence. Regarding probability: for a general understanding, we exclude deepening into the concept of probability space and other strict terms of probability theory. The consequence will be measured directly by the negative result that comes from the event.
Schematically, the main risks can be represented in Fig. 1.
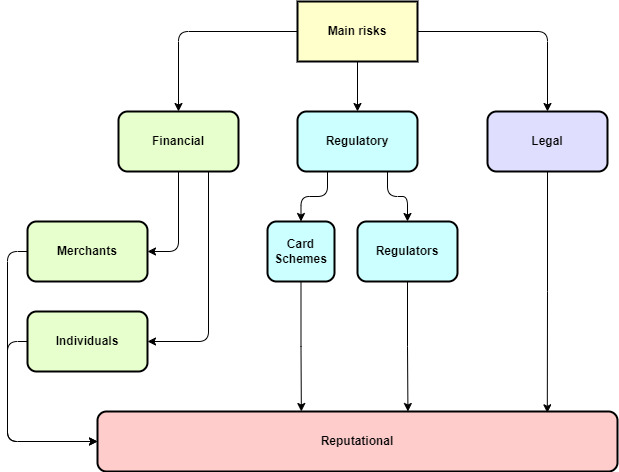
1.1. Financial risks
The palm among financial losses is occupied by losses from chargebacks. Chargeback is a procedure for refunding funds for a previously completed transaction in favor of a bank card holder. In fact, this is a refund. It should be recognized that most people, including economically active ones, who have and use several bank cards, have no idea about chargeback. This is primarily due to the fact that none of the payment participants benefits from advertising this procedure. It is not profitable for the acquirer and merchants due to objective and direct reasons — in case of receiving a chargeback, this amount is first deducted from the acquirer, who in turn, in accordance with the acquiring agreement, shifts these costs to the merchant. That is, a lost chargeback dispute is a direct loss to the merchant, and if it is impossible to reimburse this loss to the acquirer, then the latter’s direct loss. Moreover, chargebacks spoil statistics, since payment systems have set maximum permissible levels, after which the participant who exceeds this level gets into a special program that does not bode well for him. This issue will be discussed in more detail in Chapter 4.
For issuers, apart from improving customer loyalty, the procedure of disputing transactions also does not bring anything good, as it is unnecessary labour costs and various commissions. For example, if the dispute goes to the arbitration of the payment system, the losing party pays an additional commission of $500 or euro. If a cardholder disputes several transactions, the commission will be paid for each case of arbitration.
Depending on the reason for the customer’s dissatisfaction with the service or product provided, a special chargeback code is used, which is better suited in a given situation. Also, the cardholder can say that he or she did not carry out the operation, even if this is not true, the issuer is still obliged to start the chargeback procedure if its client has not directly violated the terms of the card service agreement.
Additionally, there are various fees and penalties from payment systems for violating the rules.
It is especially worth highlighting fines for illegal or prohibited activities: Business Risk Assessment and Mitigation Program (BRAM) and Visa Integrity Risk Program (VIRP). Depending on the type of violation of the rules, fines for BRAM or VIRP range from $ 25,000 to $200,000, and in some cases, disqualification of the participant is possible. These two programs will be discussed in more detail in Chapter 3.
1.2. Regulatory risks
This type of risk includes all possible negative consequences emanating from various regulators in the form of the central bank, payment systems, controlling government agencies, law enforcement agencies, and so on.
A classic example is when a payment facilitator receives a license from a financial regulator in order to accept payments but cannot fulfill the conditions of compliance with the anti-money laundering and terrorist financing policy. In addition to the direct risk of losing the license, there are many indirect methods of negative impact on the process of organizing payment acceptance.
In case of receiving a large number of fraudulent reports, the burden on interaction with banks, the police, and the regulator will immediately increase. Each of them will request information on fraudulent incidents in order to obtain all the details of the transaction for their own investigation. Victims whose payment details have been compromised by fraudsters will also contact the support service.
1.3. Legal risks
All participants of the payment market interact with each other on the basis of contracts. Anyone opening an electronic wallet agrees to the terms and conditions set out in the offer. A tick at the time of registration of the personal account means automatic acceptance of the offer. The company providing the service of replenishing this electronic wallet with a bank card has an acquiring agreement with the bank. The Bank, in turn, has contractual relationships with international payment systems. An electronic wallet has many different payment instruments, both for depositing and withdrawing funds, and each payment method is a separate agreement. Each individual contract carries the risk of non-fulfillment by one of the parties, ranging from ordinary negligence to direct intent to fraud.
For example, acquiring banks often, unfortunately, clearly abuse their position as an intermediary between the international payment system and the merchant and violate the latter’s rights to lawfully conduct claims work to defend their position on chargebacks, fines, commissions and simply possession of information. There are cases when a substantial fine is imposed on a merchant, for example, 25,000 euros for miscoding without providing any evidence base, referring to the fact that this information is closed and, in fact, forcing them to just take their word for it. Such relations and the situation as a whole are unacceptable.
1.4. Reputational risks
Any company values its reputation and all of the above risks, and their consequences have a direct negative impact on reputation. Do not underestimate the danger of a bad reputation, one negative review can scare off dozens, if not hundreds of potential customers, which leads to lost profits. For companies working in the fintech sector, it is very important to inspire confidence in their customers that their money is safe.
Even if the customer has obviously violated the rules of ownership of their electronic wallet or transferred their card data to a third party, as a result of which they lost money, a significant part of their negativity will fall on the bank, electronic wallet or other company that provides them with the appropriate product or service. Customer will sincerely write a negative review, attaching screenshots and other evidence that the «malicious» company violated their rights and deceived them. It’s human nature to look for someone to blame for your own mistakes. Therefore, along with other risk minimization measures, it is so important to pay attention to protecting your customers from phishing and generally improve their literacy when using financial products.
In addition to reputation in the eyes of individual customers, it is equally important to keep a brand in front of companies from the B2B segment. The payment world is quite narrow, reputation runs ahead of the company.
Chapter 2.
Risks posed by individual clients
In this and the next two chapters, more detailed risks from various payment participants will be shown. This chapter will begin with a review of individual clients. So, let’s take a closer look at what risks come from them.
2.1. Use of payment details of third parties
This includes the use of bank cards that do not belong to the client and hacking of electronic wallets or a personal account with funds stored there, including cryptocurrency. The main purpose of scammers in this case is to illegally enrich themselves with the help of other people’s funds.
In order to understand what countermeasures should be applied to minimize this type of risk, it is necessary to consider in more detail the nature of its occurrence. How does a fraudster get the data necessary to make payments? There are two main ways: phishing and the use of malicious software.
2.1.1. Phishing, usage features
Phishing is a collective definition, which is a kind of social engineering, in other words, it is obtaining critical and significant information in an illegal way in order to obtain subsequent benefits or direct monetary enrichment at the expense of the victim of phishing. For the first time, this data collection technique manifested itself in the mid-90s of the last century and currently the phishing technique is constantly improving.
What data are scammers most often hunting for? First of all, it is:
— bank card details;
— login and passwords for logging into various personal accounts, including bank and e-wallets;
— data required for identification, passport data, full name, date of birth and others;
— various databases.
There are a great many ways to get information, the most popular ones will be discussed below.
2.1.2. Electronic mailing of letters
One of the earliest forms. It consists in sending out information that encourages the client to provide critical information in one form or another. It is worth noting that sending emails today is not the only way for a fraudster to communicate with a victim, social networks and messengers are increasingly being used. It is difficult to predict what new methods and techniques will be used in the future, but the basics of mailing remain always the same and consist of the following:
1. Attracting attention. Depending on the execution method, a different approach is used. In an email newsletter, this is undoubtedly the subject of the letter. The name of the topic in the style of «Urgent», «Important» or «Your account has been hacked» has become non-working for a long time, the client is becoming more legible, and it is necessary to come up with new formulations. If social networks or messengers are used, then attackers often try to hack someone’s account first, so that they can then send a newsletter through the entire contact list on behalf of an acquaintance or friend. The level of trust in an acquaintance or friend is always much higher than in an outsider, and this is what the calculation is made for. In this case, the beginning of communication can begin with a banal «hello, how are you?» or immediately to the point of «help, I’m in trouble.» However, the second option is also a thing of the past, scammers try to act unconventionally and talk individually with each person.
2. The phishing itself. This is where the client is influenced in order to obtain critical data. There are a lot of scenarios, ranging from requests to threats and blackmail. The most frequent of them are appeals from law enforcement agencies, employees of financial organizations, organizers of various kinds of lotteries and other investment-attractive events. In this case, scammers use knowledge of human weaknesses, such as the thirst for profit and easy money. Knowledge of elementary psychology is also used, an attempt to instill in the victim a sense of fear for their finances. Regardless of the scenario, the text itself contains information that motivates the transfer of data. It is necessary to distinguish the distribution of text in order to receive data immediately or to enter into correspondence from the distribution of text in order to force the client to click on a link, download a file or do any other action that facilitates the download of a malicious file. In this paragraph, we are considering exactly the communication between the fraudster and the potential victim.
It is possible to attach a link to a third-party resource to the body of the letter, where the client is required to enter any data.
3. Obtaining data and further using it for selfish purposes. It should be understood that in most cases, criminals have a clear distribution by type of activity: one group is exclusively engaged in obtaining data that can be sold. Other deals with their use, for example, the purchase of certain goods or services using stolen bank card data. The third group of scammers is responsible for the sale and laundering of funds. And, as a rule, this business is international, data theft can be committed from a US citizen by persons residing in Romania, and funds will be cashed from prepaid cards in Germany. A scheme using digital money, including cryptocurrencies, can be even more complicated.
Now let’s look at the main characteristic features of a phishing email:
— the sender’s address contains an illogical set of characters;
— the domain name of the address at first glance resembles a well-known global brand or a large company, but an extra letter or number has been changed or added to the address;
— the non-standard domain zone of the sender of the letter, the domain zone belonging to some other country;
— no signature or sender’s name;
— appeals from state or government agencies from non-state domain zones;
— grammatical, stylistic or syntactic errors in the text of the letter;
— the email contains files with a non-standard or unknown extension;
— the letter was sent on behalf of the company, but the mail is not corporate, but public (gmail, yahoo, etc.);
— poor-quality design of the letter, the feeling that it was made by schoolchildren in between lessons;
— the text is in a foreign language, most often in English, since the mailing list can be made in different countries.
Some typical phishing signs in the content of the letter:
— free participation in any lottery is offered, you only need to fill in the participant’s details, including personal data;
— an appeal from an old acquaintance or friend with whom you have not maintained any relationship for a long time with a non-standard request, for example, to lend money or help in trouble;
— a message that your account has been temporarily blocked;
— appeals from law enforcement agencies in order to force the recipient to perform any actions;
— reporting suspicious transactions from a card or account with coercion to perform further actions;
— you won a prize / received an inheritance / became the winner of a quiz or competition.
2.1.3. Voice communication
In this case, a regular phone or Internet telephony is used. This type of interaction with the client is the most popular due to its maximum coverage among the population. This method works especially effectively with elderly people who, due to habit, do not always use the Internet, but nevertheless have a regular phone. Also, this group of people, due to their age, is more trusting and less informed in the field of finance, modern technologies and their use.
The stages of interaction with the client are exactly the same as with e-mailing, but with live interaction there is undoubtedly its own specifics of communication. First of all, the main focus is on solving the situation here and now. Scammers in this type of phishing are good psychologists and actors who are well aware of the specifics of interaction with a person. They try to keep the client in suspense from the very beginning of the conversation until the moment of data transfer. The main participants in the conversation on the part of scammers are also pseudo law enforcement officers, banks, government and social services. In frequent cases, the client will communicate with the person on the other end of the wire with the presence of an external background, for example, the accompanying sounds of a call center, or the speaker’s distraction to clarify information from «colleagues».
Very often, scammers allegedly transfer a customer’s call to another department or arrange for the appearance of a subsequent call from another employee. For example, initially the call may come from a pseudo-policeman who asks for some details as part of a criminal investigation not directly related to the victim. Moreover, the «policeman» himself will strongly warn that no information regarding a bank card, passport or personal data can be reported to anyone, including him, in any case. Thereby increasing the level of self-confidence. Next, a scenario is possible to warn the victim that their account, personal account or bank card data could also be compromised. Some people then take the initiative on their own and try to establish interaction with the criminal in order to ensure the safety of their funds. If this does not happen, the fraudster uses indirect questions to provoke the client to provide data. The method of erroneous assumption works very often. The client is asked the question: «According to our data, you have $ 3,013 in your account, right?». «No, you’re wrong, I checked yesterday, there must be 10 thousand, I’m saving money for my daughter’s university education,» the client replies. This trick is often used with a 3DS password, the scammer also calls any 4 digits, they say, check the code you received on the phone, the client checks and says: «No, you’re wrong, there are completely different numbers here and, as a rule, calls them».
Other scenarios are also possible, for example, an attempt to find out card details in order to transfer money for a service or product based on an ad placed by the client. As a rule, the fraudster is not even interested in the details of the product or service, the methods of obtaining it, does not ask to see the product live in advance.
2.1.4. Phishing on third-party resources
In this attack, the client takes the initiative on their own and visits any site that was created from scratch with its own design and legend. Any prize may be raffled on this site, and the user is required to fill in their details to participate in the lottery. Or make a payment for a small amount to extort bank card details from him. A fraudulent website may be created, exactly repeating the design of the original website.
The situation is deservedly unfair when, when searching for any public service, a clone site appears in the first lines of the search, where the recipient is asked to enter various data, including passport data, which then goes to the attackers. Search engines do not always keep track of those sites that pop up in the first lines, especially if this site pays the search engine for advertising. Government information surveillance services in the field of digital communications also often skip such sites due to their incompetence or other reasons. Therefore, you should not rely on the fact that a fraudulent site cannot appear in the first line of the search engine output. Finding a site on the first page of the search results does not guarantee that it has been checked by the search engine in any way.
The main features of the fraudulent site:
— there is no SSL certificate, http can be seen in the address bar of the site instead of the abbreviation https. Also, most modern browsers issue a warning about the danger in this case, or at least highlight secure sites with a padlock icon;
— poor-quality design or page layout;
— a non-standard or suspicious site name;
— an attempt to fake the name of a well-known domain. This can be done by using an additional or, conversely, skipping just one character, registering a domain in another domain zone;
— lack of contact information or outright false contacts.
It is worth mentioning separately about the ways to deal with clone sites.
If your logo, brand, commercial name or other attributes of the company are found to be copyrighted, you should immediately send a complaint to the domain name registrar and hosting provider. Most often, this is enough to block the clone site. The more information you provide in the complaint, including proving that the legitimate copyright owner is applying, the more likely you can count on a quick positive result.
In this case, contacting law enforcement agencies, the prosecutor’s office or an attempt to close the site through a court decision due to the cumbersome and bureaucratic nature of the entire legal system looks like an extremely inefficient way. After spending a lot of time and money, you can get a compulsory decision from the court to block the site, but if the registrar or hosting provider is located in another jurisdiction, as usually happens, then the price of this decision is low. In any case, it takes months, during which time the clone site will have completed all its assigned fraudulent tasks and will close itself.
2.1.5. Types of customer search
According to the type of customer search, phishing is divided into two groups: mass and targeted.
Mass phishing does not differ in any special mailing or customer call settings. Calls and mailings are made at random. The conversion rate of successful outcomes in favor of scammers with this method is the lowest. At the same time, the cost of such an attack is also minimal. It is enough to buy an up-to-date database of phone numbers or email addresses, come up with a template for an appeal or letter and send out a newsletter or call customers.
A completely different picture emerges with targeted attacks. Now you can buy almost any information about any person. Various databases are openly sold on the darknet: passport, personal data with up-to-date phone numbers and e-mail addresses, various information about a person identifying them in government and social services, for example, social security number, information about real estate, cars, etc. This information is obtained by hackers in various ways, but the main ones are malfeasance and the use of malicious software. Moreover, if using different software, as a rule, collects information about a person of a general nature, then abuse of office in a company with access to this data gives very highly specialized and detailed information.
For example, the number of open accounts for a client in the bank and the current amounts of funds on them on a certain date. Do you want to know the details of calls for a specific person? Geodata of the subscriber’s places of movement? You are welcome. You can also purchase ready-made identified customer profiles on various crypto platforms or electronic wallets for the subsequent withdrawal of stolen funds.
Millions of people work in government agencies, pension funds, law enforcement and related agencies, various departments, telecom operators, Internet service providers, banks, and data centers. There will always be unscrupulous employees among them who, due to negligence, incompetence, the human factor or for the purpose of illegal earnings, allow data leaks. All this information costs money, so targeted phishing is good to use for wealthy clients.
There is also a combined scheme, when an additional point purchase of the necessary information is applied among identified and ready-to-cooperate customers obtained through mass phishing. There are also a lot of open government resources where you can check various information by entering data about a person: the presence of debts, participation in legal proceedings, fines, etc. All this allows you to create hundreds of scenarios for voice or electronic phishing individually for each client.
Even if a person is sufficiently educated and experienced in the financial field, a call from, say, their insurance agent, who has absolutely all the information on their profile and data, can be very misleading and endear this person to the caller. And then it’s a matter of technique, under what pretext and what data to extract. In most cases, when the client hears that the caller knows the passport and contact details, they are ready to share any missing information, including access to personal accounts of financial institutions, bank card numbers, incoming SMS with passwords. The trick of verifying passport and contact data is used quite often, the fraudster asks to verify their relevance and dictates absolutely correct and up-to-date data himself. This performance against the background of the noise of a «working call center» convinces the most doubtful skeptic that a legitimate employee is really calling.
2.1.6. The use of malicious software
This type of obtaining critical customer data is very common, and very insidious, because it happens without the knowledge of the customer himself. We will not pay much attention to this issue in the book, since this aspect lies more in the plane of information security. Nevertheless, it is worth mentioning the basic precautions:
1. Use of licensed software, including antivirus protection systems. Keeping them up to date.
2. Two-factor authentication is required for all critical accounts. Recent research in the field of information security has shown how easy it is to intercept an SMS message with a confirmation code, which is available almost all over the world, as it is transmitted via the SS7 protocol. In fact, any system can be accessed via SMS with a confirmation code, even with two-factor authentication enabled.
How to protect yourself:
— opt out of two-factor authentication via SMS when the confirmation code arrives in a text message. It is better to use the application to generate.
3. Public Wi-FI networks.
An elementary attack with a key reset leads to the router connecting to the hackers’ network. All data downloaded or transferred when connected to the network, including private keys, becomes available to hackers. This is especially true in airports, hotels and other public places with large crowds.
Also, anyone with a mobile phone or laptop can share their network, make it free, and use simple manipulations to collect a lot of data, including critical ones such as card numbers, document details, passwords, and so on. For example, at Istanbul Airport, an attacker can rename his personal network to «Istanbul_Wi-Fi_Free» and distribute it for free. Many people will connect to it without thinking about any security measures.
How to protect yourself:
— Never perform critical actions using public Wi-Fi networks, especially if this network is not password protected;
— regularly update the firmware of your own router, as manufacturers are constantly releasing updates to enhance protection against key substitution.
4. The use of various bots in messengers, including money transfers or the purchase and sale of cryptocurrencies.
Most often, such a bot notifies the user about a problem with their crypto assets, trying to force the user to click on the link and enter a private key, thereby the owner will permanently lose their funds.
How to protect yourself:
— ignore the activity of bots, think about each of your responses to the offer;
— protect your messenger channel with antivirus software;
— complain to the chat administrators about any suspicious activity.
5. Various plug-ins and extensions in the browser.
Modern browsers offer various solutions to the user for more comfortable work. And the problem is not only that extensions can read everything you type while using the Internet, most of them are written in JavaScript, which is especially susceptible to cyber attacks.
How to protect yourself:
— do not download any third-party extensions;
— use only licensed official browsers.
6. Fake apps.
The victims are often owners of Android devices who do not use two-factor authentication, as it requires not only a name and password, but also additional information known only to the user.
How to protect yourself:
— do not install unfamiliar mobile apps unless absolutely necessary;
— enable two-factor authentication for all apps on your smartphone;
— be sure to check the link to the application on the official website.
7. Unknown flash cards or other storage media. It is no secret that many organizations do not have any input or output devices at all that would allow recording or inputting information from external storage media. This refers to all sorts of slots for floppy disks, flash cards, and other storage media. But such requirements are not applied everywhere and are mainly related to sensitive facilities or government agencies. Many financial institutions do not have such a practice. An intruder can order the production of, for example, several flash cards with the logo of a well-known bank and leave them unnoticed in different branches. The hope is that some employee will mistake this flash card for a corporate one and try to see what is there. Malicious software can be placed on the media itself, disguised as some kind of service file, for example, a simple document with the title «The Company’s Development Strategy for the current year.» Or «Salaries of employees of the Information Security Department.» The calculation is based on human interest. There is a possibility that one of the employees will open the file.
How to protect yourself:
if the Company’s policy does not restrict the input and output of data from employees’ computers, then it is necessary to include such examples in the mandatory annual staff training.
Special attention should be paid to the topic of differences and features of fraud using crypto wallets. The private key can be compromised in any way specified above. For scammers, hacking a wallet and transferring cryptocurrency is more attractive due to several reasons:
1. In many cases, you will not be able to restore the private key. If it is lost, you may never regain access to the funds in your wallet.
2. It is extremely difficult to prove the theft of funds from a crypto wallet, most owners get wallets for themselves without passing any identification. When money is stolen from a card, it can be unequivocally proved, including with the attachment of an official bank account statement, the fact of the transfer of funds and their belonging to you as a bank customer. This is more difficult to do with cryptocurrencies, and law enforcement agencies and courts are reluctant to work with this kind of evidence. Especially if such a document was issued by an unlicensed crypto exchange or an exchange located in another country. In many cases, this happens.
3. All payments made using blockchain technology are final and non-refundable. Payments made by mistake or unauthorized cannot be refunded. Also, unlike a bank card, you will not be able to go to the bank and apply for a refund due to fraud (chargeback).
4. Filing a police report in this case is not an action that can increase the chances of getting your funds back for the following reasons:
— the legal status of cryptocurrencies in many countries has not yet been fixed;
— it can be difficult to prove the ownership of a hacked wallet, and in some cases it is impossible (see paragraph 2 above);
— it is also not possible to find the recipient, if for all fiat transfers you can make a request to a bank or other credit institution, because all transfers using electronic means of payment are regulated, then in the case of crypto currency there is no regulation in most countries;
— it will be almost impossible to prove the fact of coercion or unauthorized transfer of your funds.
2.2. Laundering of illegally obtained funds and financing of terrorism
When it comes to money laundering, most often there is an association with a company, a legal entity or even a group of companies. However, this risk also comes from individuals. The main schemes and methods of countering them will be discussed below.
Given the fact that there are combined schemes, it makes sense not to describe these risks separately for companies and individuals, but to consider them comprehensively.
The following criteria should definitely attract increased attention and be further investigated:
1. The country of the card where the payment is made is high-risk. The list of high-risk countries will be different for each business. Nevertheless, there is an official gradation of countries by risk in an organization called FATF — Financial Action Task Force. At a minimum, when compiling a list of high-risk or banned countries, one should be guided by the rules and recommendations of this organization.
2. Iterating over the same parameters in different transactions. This criterion refers to those cases when using the same parameter, for example, an IP address, many operations are performed with different unique identifiers, such as an e-mail address, bank card number, wallet number, crypto address, and so on. Of course, a person can have two emails, 5 cards or three phone numbers. Or three relatives or several colleagues and friends can make transactions from one IP address or one device within an hour. However, these situations are rare, and for scammers, such behaviors, on the contrary, are very common.
3. Using a large number of cards. A very common scenario. Despite the large number of virtual disposable cards, the lion’s share of users does not have more than 3—4 cards. It is also worth considering the time period during which these cards were used. The smaller it is, the more suspicious the user’s behavior looks. In this case, of course, it makes sense to pay attention to other factors: cards of the same country or different, whether all cards belong to the same bank or even BIN, which cards are used, virtual or not, etc.
4. Attempts to disguise the client’s profile in the account. For example, the lack of information in some fields, or filling in test or obviously meaningless data in those fields that are required to be filled in. An example of such a filling can be: 111111111, rfiejhvwserhuji, etc.
5. Attempts by the user to hide their location by using various tools. This means using proxy servers, temporary virtual phone numbers or email addresses to register an account, specifying the wrong country of residence, etc. That is, this is not a direct falsification of data, this is a completely legitimate attempt to hide geolocation information, as well as all traces that can be used by law enforcement agencies if necessary to establish the identity of the client and its true location.
6. A large spike in transactions by the client in a short period of time for no apparent and logically justified reason. Especially if this does not correspond to the initially stated turnover when onboarding the client.
7. Checking the user’s behavioral factors. Non-standard conduct of the client, for example, when they refuse a more favorable offer, buys several similar models of phones or other easy-to-sell goods at once, buys a large number of different tourist vouchers for different people, etc. All such deviations must be calculated and described in the logic of the anti-fraud system.
8. The use of forged or invalid documents to identify the user. Actually, this point is rather not from the category of suspicious criteria, but direct violations. After that, the client should be blocked immediately. However, there are nuances here too. It happens that a person tries to be identified with an invalid document, for example, a foreign passport, or a husband registers an account for his wife, sends documents in her name and does not pass identification at the stage of checking a selfie. There is not always malicious intent here, such a case can be quite standard. But in the case of an attempt to send a fake document or a drawn one, or to an absolutely unrelated person — here, of course, such cases should be considered as fraud attempts.
9. Suspicion of falsification of card data through the use of photo editors. It is not always possible to accurately determine that the provided photo of the card is fake. It is especially difficult to detect this when taking screenshots with virtual card data, in this case, the use of a photo editor becomes almost invisible to the verifier. Embossed cards are the easiest to check because of the volume of the indented characters or numbers. They are more difficult to identify, but, nevertheless, they are also suitable for checking physical cards that are not made in an embossed way, but simply with information printed on the card. There are no indented symbols on such cards.
10. Splitting payments in order to legalize (launder) proceeds from crime. Each country has its own limits, restrictions and a set of criteria for identifying suspicious and mandatory transactions. There are also generally recognized international standards and criteria. Scammers use both simple limit circumvention schemes and more sophisticated ones. Simple methods include the classic splitting of payments, in order not to exceed the maximum allowable amount subject to mandatory control. For example, there is a limit on the maximum amount of an operation of 40,000 euros per month. If this limit is exceeded, the client, according to the AML policy, must provide additional documents and information and undergo an in–depth verification — EDD (Enhanced Due Diligence). It is necessary to withdraw 500,000 euros obtained by criminal means and/or that will be used to finance terrorism. The easiest way to make transactions every month that do not exceed the established limit. But it will take more than a year, moreover, there is a chance that you will still get an in-depth check if the financial institution has not only a monthly limit, but also a limit for a longer time, for example, a quarterly one. It is more effective not just to split payments, but to create fake accounts under the control of the very client who owns the principal amount, or to create real customer profiles (drops), which will nevertheless also obey, for certain commissions, the main owner of the funds. However, such a path requires significantly higher costs from the criminal.
11. Frequent chaotic change of the IP address, phone number and (or) other identifier of the device from which the user accesses their account. This can also happen in everyday life, when attackers gain access to mail or phone, after which the client wants to replace the compromised data. Nevertheless, this should also be alarming, as it indicates a negligent attitude of the client to their usernames and passwords. Fraudsters can also change their email or phone in order to cover their tracks or confuse the investigation, for example, register with their own data, then try to change them to fictitious ones.
12. Unjustified delays in the provision of documents and information by the client that cannot be verified. Often, suspicions are aroused by those documents that are provided extremely quickly or, conversely, extremely long. In the first case, this may indicate that the client uses template documents and changes only some data in the photo editor. Let’s assume that there is a group of scammers who use front people to launder funds from their bank cards. All cards are of the same type, as a rule, even one or two banks. To withdraw funds, several templates are used — bank account statements and a screenshot with a virtual unnamed card. A screenshot can be faked using a picture with the details of the card taken in any graphic editor. It is much more difficult to fake a photo of the screen of the device that shows the card or its data. It is worth considering this when checking. Let’s go back to the drops. When requesting an account statement and a photo of the card from them, they can send it very quickly, literally within 5—10 minutes, since a ready-made bank statement is used for the template, in which only the client’s full name and their card number change. The situation is also with the forgery of a virtual card. Given the fact that a lot of accounts are created, and one or more people are doing this, they want to put the provision of the requested documents on stream and not wait specifically for an hour or even more, as is required for the average client.
The flip side of the coin is the unreasonably long provision of documents, which may also indicate that the client is trying to find a way to forge a document, especially if their behavior indicates that they are in a hurry to make a transaction. Or it may be a refusal to send a selfie with a document, motivating it for various reasons, sometimes the most ridiculous, for example, a refusal to send a selfie because the client claims that she is not made up. The long provision of an agreement between two legal entities or several similar companies should also alert the inspector, as a rule, such agreements are stored in a structured manner, and it is not difficult to scan them, especially if the client himself shows haste or nervousness when communicating with support.
13. The history of user interaction within the same account. Of course, a client with a history deserves more trust than a newcomer. Nevertheless, there are cases when, for example, a merchant opens an account, connects to acquiring, makes small turns during the year, after which it mixes or substitutes illegal or prohibited traffic. The auditor’s mistake in this case will be a biased attitude towards conducting an in-depth audit due to the fact that the merchant has already been working with their organization for a whole year and no problems or fraud reports have been received on it.
14. The inconsistency of the operations carried out by the client with its initially stated goals and type of activity. The client can declare that the company is engaged in a legal white and not risky business, but in fact carry out prohibited or high-risk transactions that either cost more in exchange (transaction fee) or carry a direct risk of receiving fines from international payment systems, regulators or other regulatory institutions. Also, according to the AML policy, it is necessary to assess the risks for each client as correctly as possible, and this is not a bureaucratic requirement. In reality, it helps not only to earn more, but also to reduce risks at the same time.
15. A large number of test operations that cannot be explained by common sense or simple logic. From the very beginning, you can get an idea of the upcoming traffic from test transactions. Obviously, attempts to test payments from those countries that are either closed at all or have been declared by the client as unnecessary for their business will be suspicious. There are also cases when transactions for the same amount, for example, $ 55, are issued by the merchant as test ones, trying to justify the situation with such payments, but in fact it may be the sale of a prohibited or prescription medical drug of exactly this value. In relation to individuals, at the testing stages, you can notice numerous attempts to pay with cards issued in other people’s names or receive bank transfers from various senders. This may be the preparation and testing of the system for further acceptance of payments related to money laundering or an attempt to withdraw funds with questionable origin.
16. Excessive persistence of the client in trying to use your service. Do you have the most favorable conditions in the market? Is there a lot of competitors in your field, but at the same time the client is persistently asking for you? This is also a red flag.
17. The absence of the client’s interests in defending their rights in dispute work in accordance with the rules of international payment systems. What is meant by that? When a merchant receives a chargeback with any code, it is extremely interested in winning this dispute. To do this, the merchant actively participates in the formation of a package with documents proving its correctness and comprehensive provision of services to the cardholder. The reverse picture can be seen if the merchant sells something illegal, for example, unlicensed gambling or drug sales. In this scenario, the merchant tries to resolve the conflict by any means without bringing the dispute to arbitration and a more detailed study by the payment systems. Also, the merchant does not want to anger the client, provoke them to contact law enforcement agencies or write various complaints on the Internet, thereby revealing the true activity. Such cases are characterized by an unreasonable number of refunds for any reason, regardless of whether the service has been provided, or the goods have been delivered. The rule is simple: if there is a complaint, the merchant makes a refund. This can be detected by the corresponding limits set on the number of refunds in absolute and relative to turnover values.
2.3. Friendly or Family fraud
This type of fraudulent transaction is called friendly or family-friendly due to the fact that for the simplest explanation, a case is given when a customer accidentally or intentionally paid for a purchase using a friend’s or family member’s card, who subsequently stated that they did not make these transactions. In practice, the vast majority of cases are deliberate cases of fraud of issuers by legitimate cardholders. That is, they authorized the transaction themselves, and later, for the purpose of illegal enrichment, they try to deceive their bank. This applies not only to a bank card, but to any type of payment, whether it is a bank transfer or an electronic wallet. But this method is most common on bank cards, since the issuer is obliged to accept a fraud statement from its holder, log it into the system and send it to the acquirer, and if necessary, dispute this transaction by initiating the chargeback procedure. The scammers are counting on the latter. Moreover, this fraud often has a successful end result for the fraudster, and these reasons should be considered in more detail:
1. Incompetence of employees in the field of risk management or AML. Sometimes there are problems with assessing real risks, rather than potential ones. For example, a recall (in fact, a request for a refund) was received from the sending bank of the payment with the motivation that the legitimate sender did not send the money and this is a fraudulent transaction. During the verification, it may be revealed that the sender’s name does not match the recipient’s name, although according to the description from the sender’s bank, the service itself implied the transfer of its own funds, respectively, the service was not provided or was provided in violation of regulatory requirements in the field of customer identification. A comment from the sender’s bank can be any, including one that does not correspond to reality, because the bank is interested in satisfying its client, therefore it itself can contribute to fraudsters.
Suppose that after checking this case, it turns out that there are no connections with other transactions, there are no intersections with other clients, the client has been identified, was checked against lists for belonging to PEP (Politically Exposed Person) sanctions, and so on. What is the risk in this situation for the recipient’s company in case of refusal to return funds to the sender? None at all. Of course, you can fantasize about potential risks, especially if the client complains to the central bank, threatens to go to court, the police, so that they open a criminal case, and so on. Nevertheless, such cases of refunds are very common, related to the incompetence of employees and/or ignorance of their own processes in the company.
2. Fraud on the part of the issuing bank. The customer pays for a product or service using a card on a website that does not support the use of the 3DS protocol. The customer does not receive this service or product. Next, they come to the bank and declare that the goods were not delivered to them. The bank employee sees that the transaction took place without 3DS, accordingly, the merchant will be responsible for fraudulent chargebacks. The probability of winning such a chargeback and successfully returning the money to the customer is much higher than using a dispute code related to non-delivery of goods. The issuer deliberately commits this deception and declares the transaction fraudulent.
3. Not using the 3DS protocol. In favor of better conversion, some merchants deliberately open a terminal without 3DS. In general, such a concept would be quite workable if it were not for scammers who specialize exclusively in this type of fraud. They are constantly looking for such merchants, run cards through them without using 3DS, after which they declare fraud, win chargeback and illegally enrich themselves. Suppose a Forex merchant gives a turnover on a non-3DS terminal of $ 10 million per month. You can earn 1% on the commission from acquiring. It turns out 100 thousand per month. It is enough for several customers with a turnover of 30 thousand on the card, who will eventually declare their transactions fraudulent and ask the bank to initiate chargebacks in order not only to kill all profits, but also to get into the payment system’s program for exceeding fraud thresholds. And for carders, this is just a gold mine, because they can earn as much at a time as the average citizen earns in a whole year. Therefore, the rejection of the 3DS protocol in the field of high-risk merchants always carries a similar risk, which should be taken into account, and if possible, be able to calculate, when building such a payment acceptance model.
The problem of identifying family fraud
It is very difficult to identify this type of fraud as a result of monitoring or when using an automatic anti-fraud system. The reason lies in the very nature of this type of fraud: people, as a rule, make a purchase themselves, which means that all their behavioral factors will not arouse any suspicion. They use their IP address, email, phone, and identification data. No anti-fraud system can read a person’s thoughts or intentions, especially if at the time of the transaction they did not even think that after some time they would decide to declare this operation as fraudulent. There are also no links to other fraudulent transactions, as collusion is not typical for family fraud. Nevertheless, after receiving the first fraud reports and suspicions of their belonging to family fraud, it is necessary to look for characteristic signs and make changes to the settings of the anti-fraud system.
Chapter 3.
Risks posed by merchants
In this chapter, I will reveal the various scenarios that can happen when providing payment processing services to merchants.
3.1. Deception of customers or misleading
At first glance, it may seem that this is a small risk. If this happens periodically or accidentally, then yes, it has little effect on the business and is rather a standard situation for any merchant. However, it is worth considering cases where this is done intentionally. Below we will look at some examples for a clearer understanding:
1. Deceiving users from the very beginning.
Let’s assume that the merchant has passed the initial verification and has started accepting bank cards for payment. This can be a regular delivery of goods at an attractive price. Customers buy, wait for delivery for several days, and start calling the merchant. The merchant manages to convince them to wait for some more time, motivating the delay with problems at the logistics company. After two to three weeks of waiting, it is possible to receive the first fraud reports from issuers or directly from users who were unhappy that the product was never sent to them. There are no chargebacks yet, as issuers refuse to accept applications from their cardholders at an early stage, citing the rules of international payment systems, as well as the need to continue correspondence with the merchant, since it does not refuse to deliver the goods, these are just temporary difficulties that will be resolved in the near future. The issuing bank may also recommend making a refund and, if the refund does not arrive on time, then apply for a chargeback. The first and second options take time and give the fraudulent merchant quite a comfortable feeling while continuing to deceive people. So, already in the second or third week, you can receive alarm calls about the merchant’s work and take the necessary steps to verify. For example, requesting documents from a merchant proving that the goods really should have been shipped, but there are some problems in delivery. After the assessment, it is worth determining whether this is really a temporary problem or just a fraudulent trick. In any case, it makes sense to disable the merchant’s payment method via bank cards, leaving alternative irrevocable payment methods until the situation is fully understood and user complaints are satisfied.
Suppose the merchant is disabled, however, after some time, chargebacks will begin to arrive, which in such a case can be up to 50% or even more. If the merchant turns out to be a fraud, all these chargebacks will be lost, and the amounts withheld will be almost completely a loss to the company providing the acquiring service to this merchant.
2. Failure to provide services to users in the long term.
This situation differs from the previous one by a much higher risk of financial losses. Due to the fact that over a longer period of time, more customers will be deceived or will not receive their services that they expected. As a rule, there are only two types of such scenarios: deliberate deception and a combination of circumstances. Both options are equally dangerous, with the only difference that in the case of deliberate fraud, the beneficiaries acting on the part of the merchant are more difficult to find, because they made attempts in advance to hide their location, identification data and the ability to obtain this information, for example, by the police when searching for them. In the first case, a classic pyramid scheme can be used as an example. It can be expressed as the acceptance of funds for trust management (including without appropriate licenses from the regulator), forex activities or binary options, investment offers with several hundred percent per annum, and so on.
Financial pyramids exist because of the deferred end. By attracting new funds, debts to previous clients are paid. This, firstly, creates the appearance of legitimate activity for the investor, and secondly, allows the pyramid to scale the business, attracting more and more money.
Conditionally, if a company has to pay dividends to a hundred customers in the previous month, then by attracting 200 in the current month, it can both pay off debts and invest funds to attract even more investors next month. Moreover, the progression in these schemes is usually geometric. All financial pyramids are falling apart mainly for two reasons.
The first is the problem of attracting enough funds to pay out to previous depositors. The second is the decision of the founders of the pyramid to quit the game, or some external reasons that do not contribute to the continuation of their activities. Eventually, the pyramid collapses, and for the acquirer or payment facilitator, the following happens. Chargebacks are received using the code «Goods or Services Not Provided». The acquirer’s side is trying to contact the merchant, but it has either already disappeared or cannot/does not want to provide this evidence. The first chargebacks are won by cardholders, after which information is distributed among those depositors who actually received money, and the service was provided to them in full. But knowing that the merchant has disappeared, they turn into the type of scammers that we described above: friendly (family) fraud. That is, they, in fact, want to illegally enrich themselves. For the acquirer’s side, this means not only financial losses for those users for whom the service was not actually provided, but also for many other dishonest clients of the former financial pyramid. Given that the chargeback code «Goods or Services Not Provided» in most cases can be submitted within a year and a half after the transaction, the amount of lost funds can be fatal for the continued existence of the company that accepted this merchant for service.
As an example of the second case, related to the unintentional non-provision of services to the client in the long term, consider the sale of concert tickets and tourist vouchers. Both types seem at first glance completely harmless and safe for business. The organizer can sell concert tickets six months in advance, and the event itself can be canceled for various reasons, up to the whim of a celebrity a few days before the concert. In such cases, there are problems with refunds, and payers initiate a chargeback. There are also many scammers in the field of ticket sales, so it is very important to check all agreements with the organizers, ways to sell tickets, lease agreements for sales offices, website ownership, and so on.
Three types of companies are engaged in the sale of tourist vouchers: tour operators, travel agents and companies that have nothing to do with the first two, some intermediaries. But they are usually scammers with the original intent, and we will not consider them here. Some people also buy travel packages in six months, and even if large licensed tour operators are declared bankrupt from time to time, then what can we say about agents. They are representatives of the same tour operators, but since this is an additional link in the chain, this scheme of selling vouchers is riskier for the acquirer. The risk here also lies in the inability, after the sale of the tour package, to provide this service to the buyer, who then initiates a chargeback. And since this sales period can easily reach 6 months, the amounts of disputed transactions can be very impressive.
3.2. Covert conduct of illegal activities
Each merchant is checked during the onboarding procedure, regardless of the payment methods that will be available to him: bank cards, electronic money transfers, cryptocurrency, bank transfers or any others. The greatest risk for a payment processing company is precisely bank cards, however, other payment methods have their own specific risks, which come primarily from regulators and supervisory authorities. However, if the merchant is checked for all possible risks for accepting bank cards, this check will cover other payment methods in most cases. So, it makes sense to start with bank cards. One of the significant risks for a company accepting bank cards is non-compliance with the requirements of payment systems and getting into special programs.
Business Risk Assessment and Mitigation Program (BRAM).
Бесплатный фрагмент закончился.
Купите книгу, чтобы продолжить чтение.